Configuration of Hideez Cloud as an External Authentication Method for Microsoft Entra ID via OIDC
Hideez Identity Cloud - Configuration OIDC for Entra ID as an External Authentication Method
Configure OIDC for Entra ID
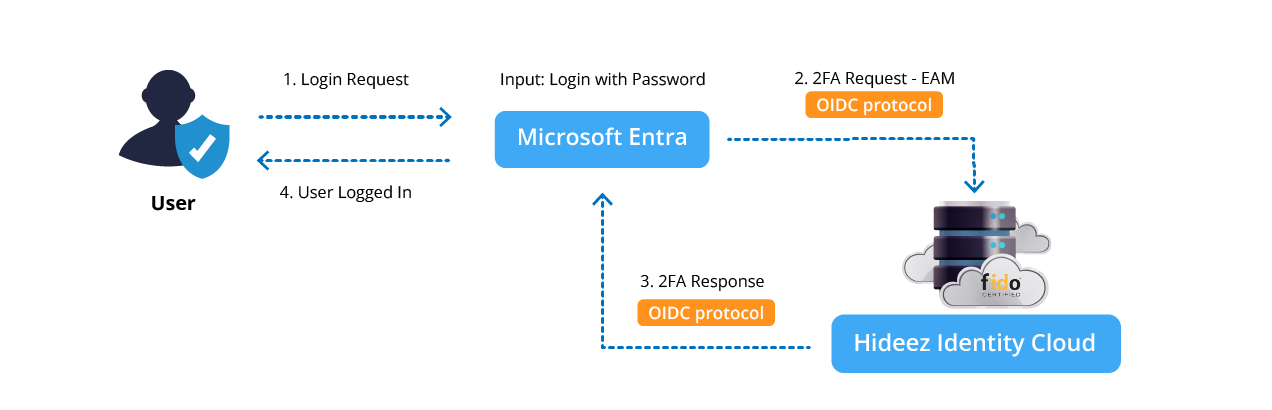
This guide provides step-by-step instructions to configure Hideez Identity Cloud as an External Authentication Method (EAM) for Microsoft Entra ID using OIDC (OpenID Connect). This setup facilitates seamless external authentication and ensures secure user login through an additional MFA (Multifactor Authentication) step.
Important Notes
Hideez Server as an External Authentication Method (EAM) does not enable direct login to Microsoft Entra ID. It serves solely as an additional MFA verification method.
This functionality is only supported for standard user accounts. Using Hideez Identity Cloud as an EAM is not possible for administrator accounts.
To enable this feature, an Entra ID P1 license is required.
Additional Resources
For further setup guidance, refer to the following articles:
Step 1: Register the App in Microsoft Entra
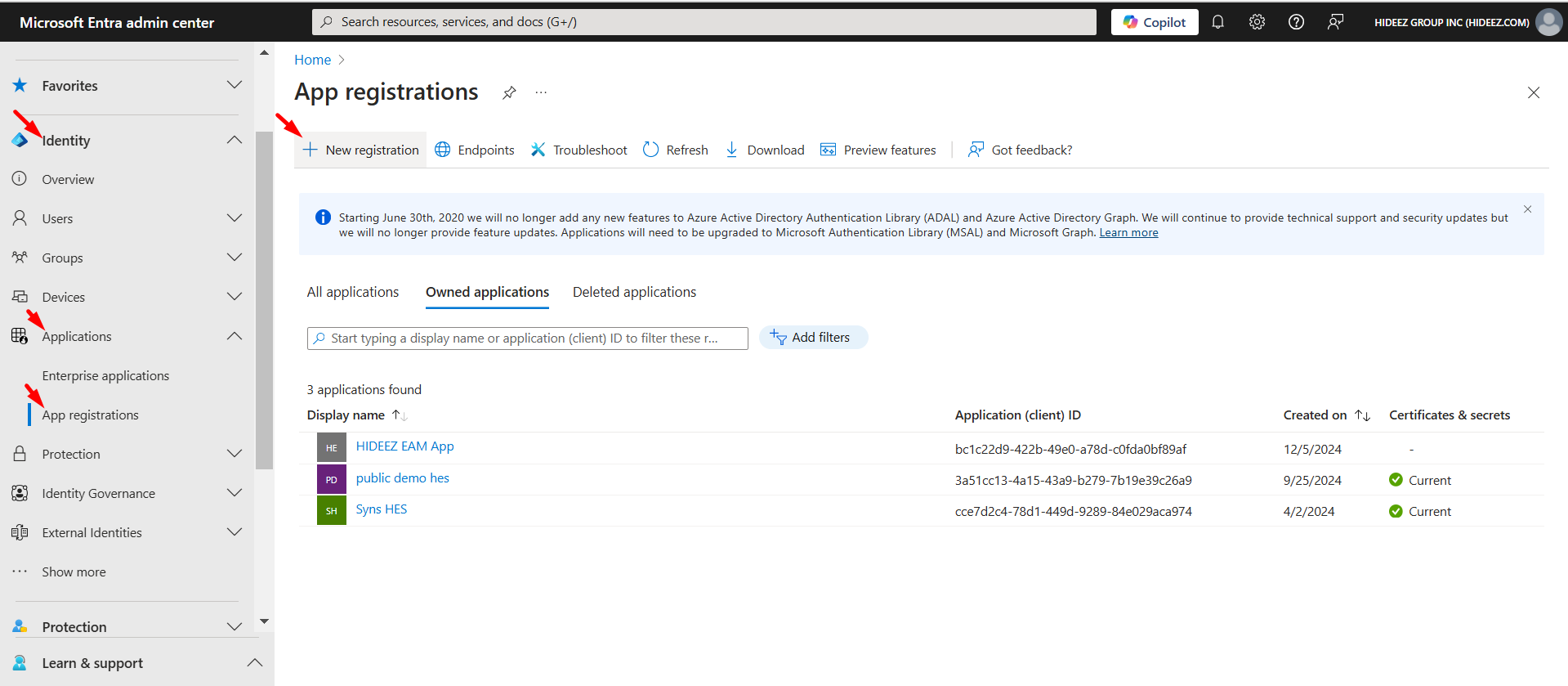
Log in to the Microsoft Entra Admin Center.
Navigate to Identity → Applications → App Registrations.
Click + New registration.
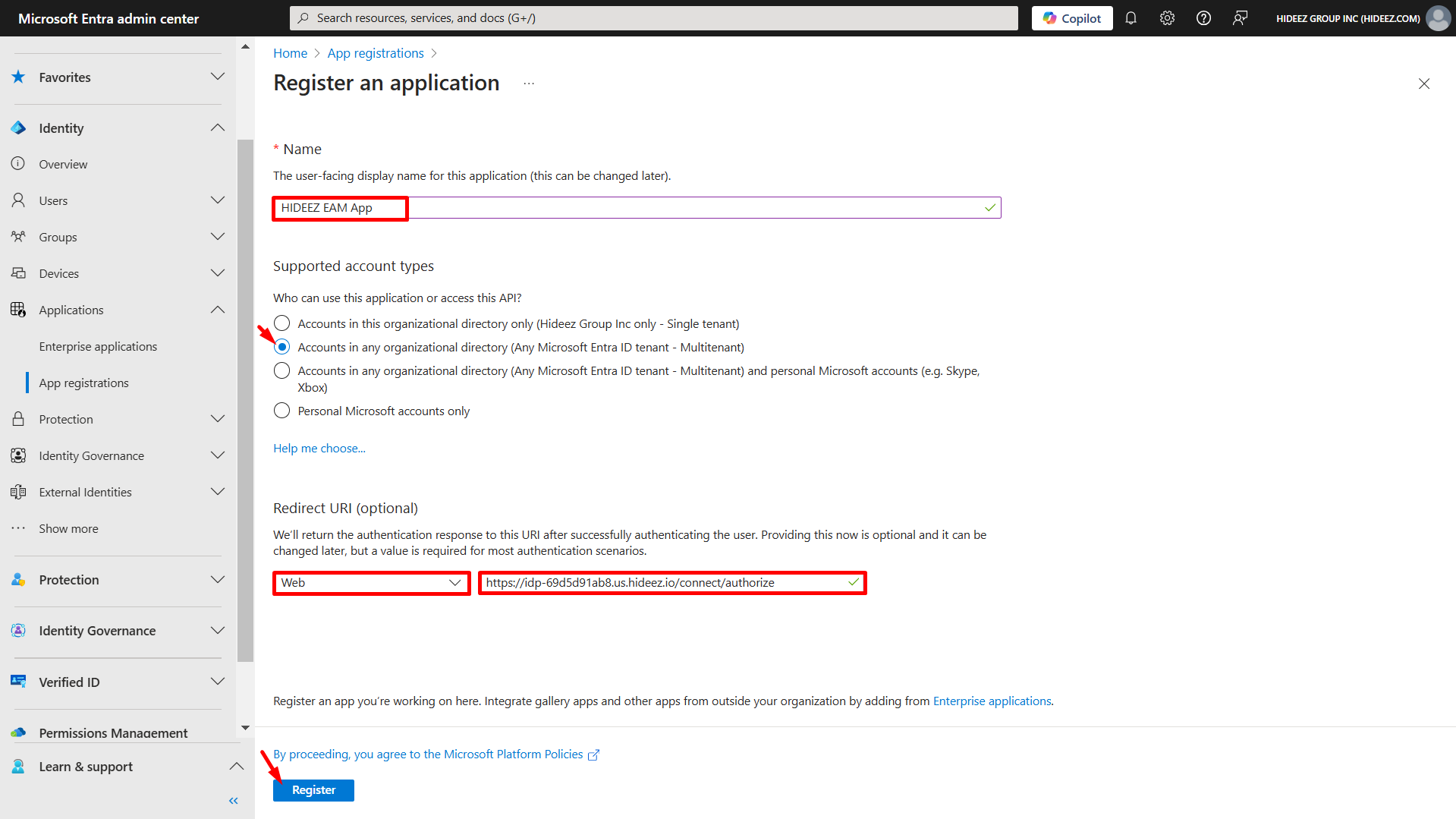
Define a name for the app.
Set Supported account type to:
Accounts in any organizational directory (Any Entra ID directory - Multitenant).
Under the Redirect URI section:
Select Web platform.
Enter:
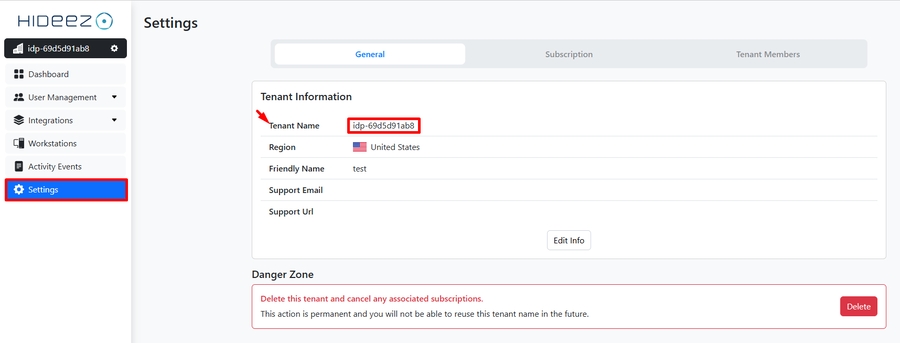
https://<Tenant Name>.<us|eu>.hideez.io/connect/authorize.Example:
https://idp-69d5d91ab8.us.hideez.io/connect/authorize.
You can find the Tenant Name in the Hideez Identity Cloud in the Settings section:
Click Register.
After registering, keep the Application ID from the Essentials section. You'll need it later to configure your EAM in Hideez Cloud.
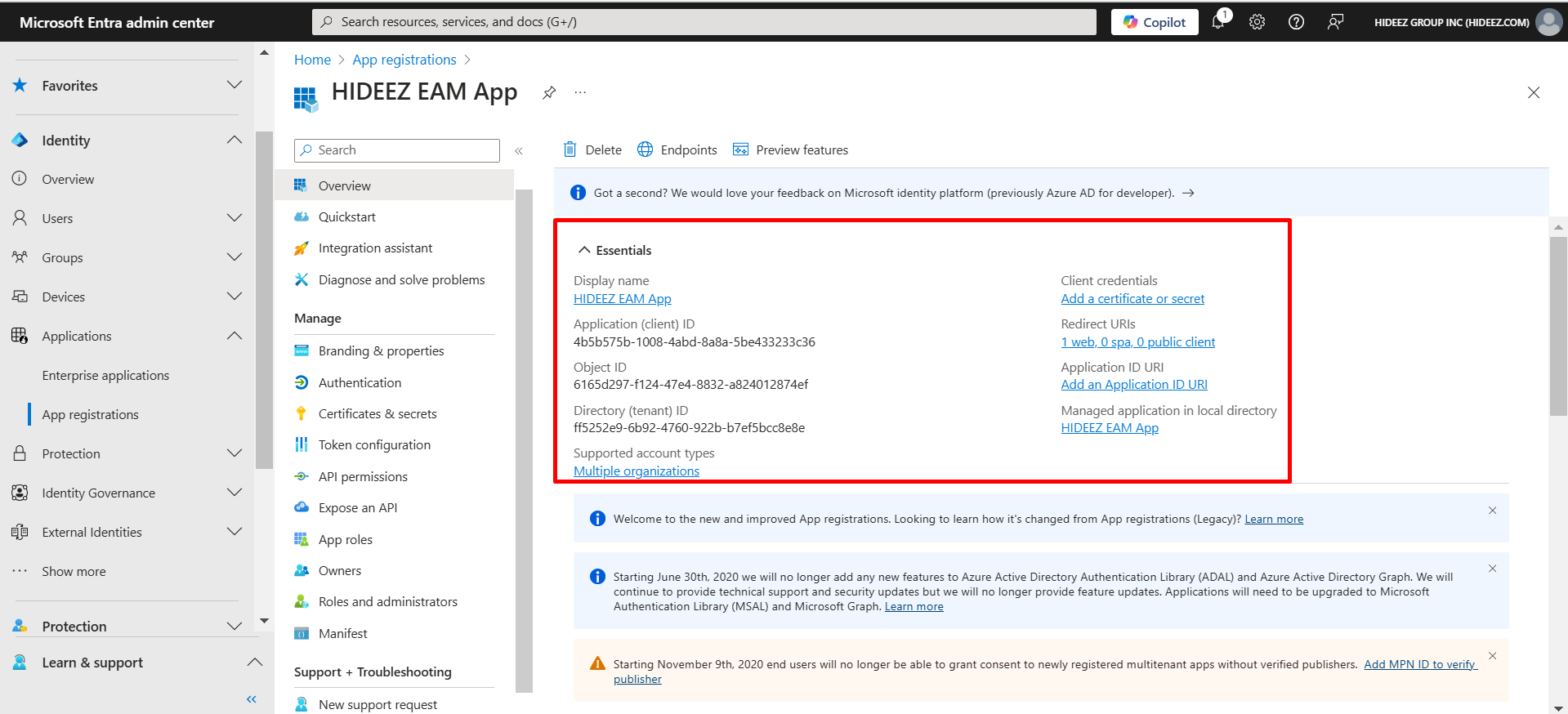
Step 2: Configure Integration in Hideez Cloud
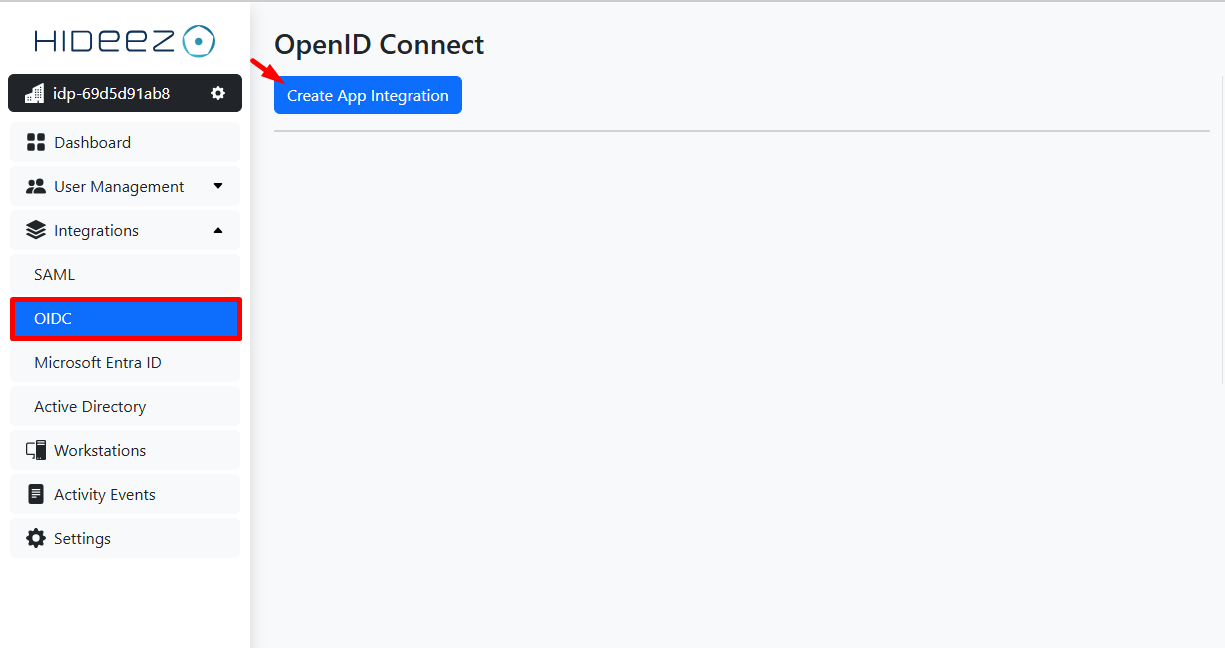
Go to Hideez Cloud.
Go to Integrations → OIDC.
Click Create App Integration and set the following parameters:
App Type: Entra ID External Authentication Method (EAM).
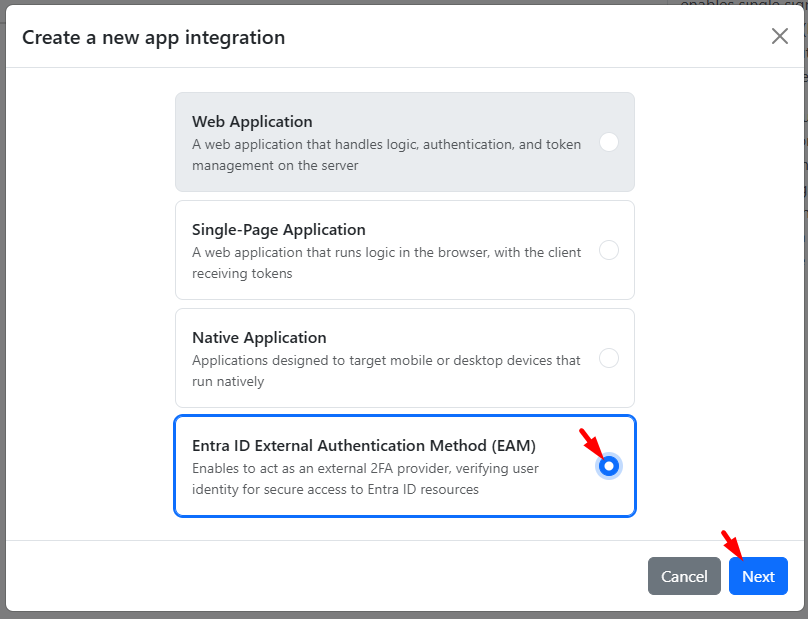
Fill in the following:
Tenant ID
Application ID
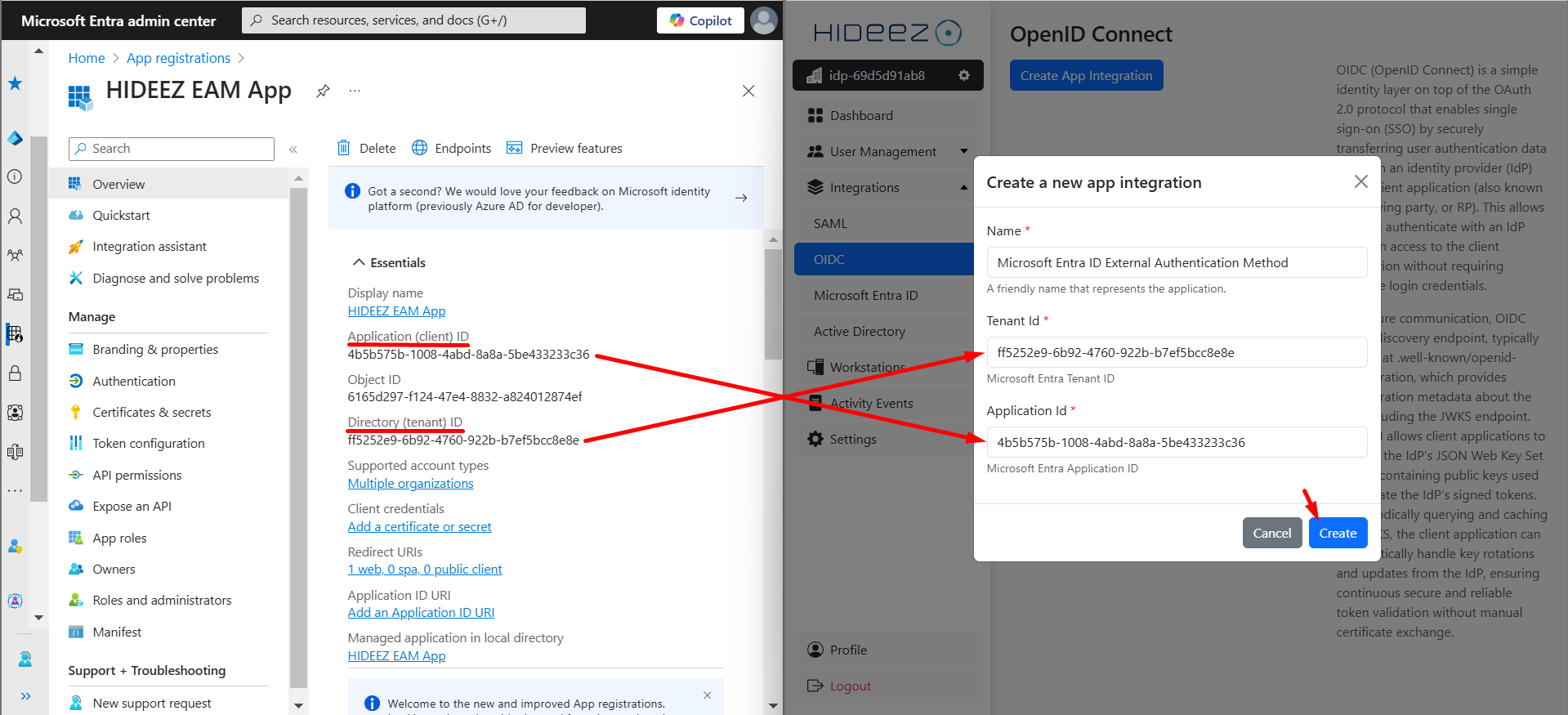
Click Create.
Keep the tab Settings with values Client ID, Discovery Endpoint, and Entra Application ID ready for the next step.
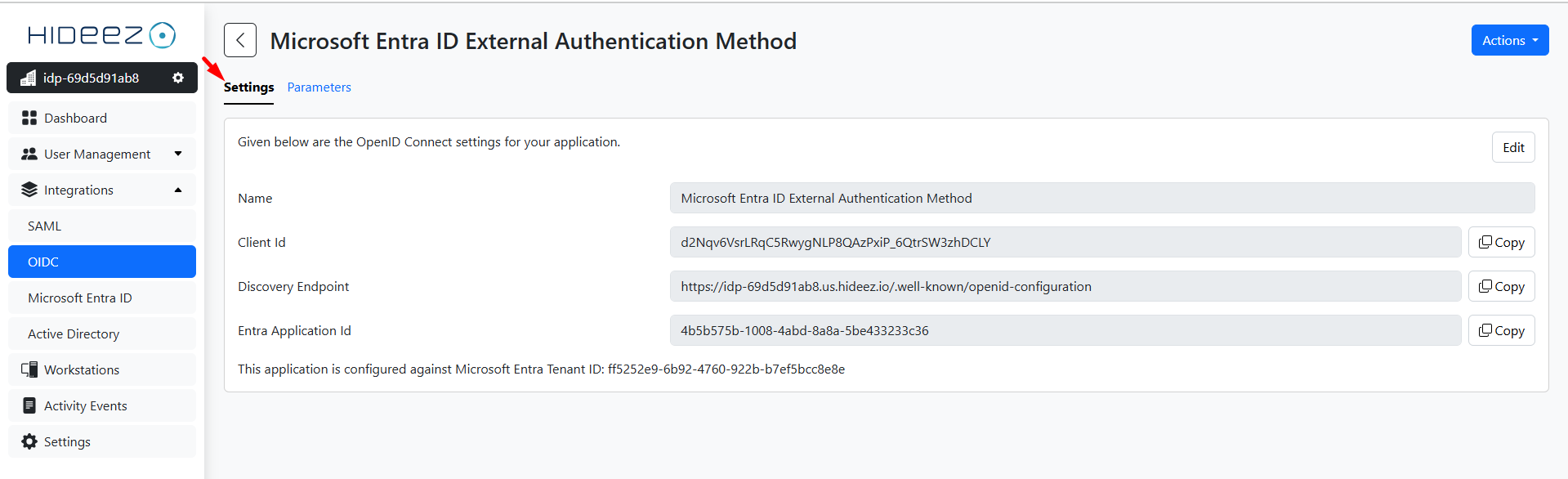
Step 3: Add External Method in Entra ID
Go back to Microsoft Entra Admin Center.
Navigate to Protection → Authentication Methods → Policies.
Click + Add external method (Preview).
Set the following parameters:
Name: The name users will see during Entra ID login when choosing their authentication method.
Client ID: Paste from the app integration in Hideez Cloud.
Discovery Endpoint: Paste from the app integration in Hideez Cloud.
App ID: Paste from the app integration in Hideez Cloud.
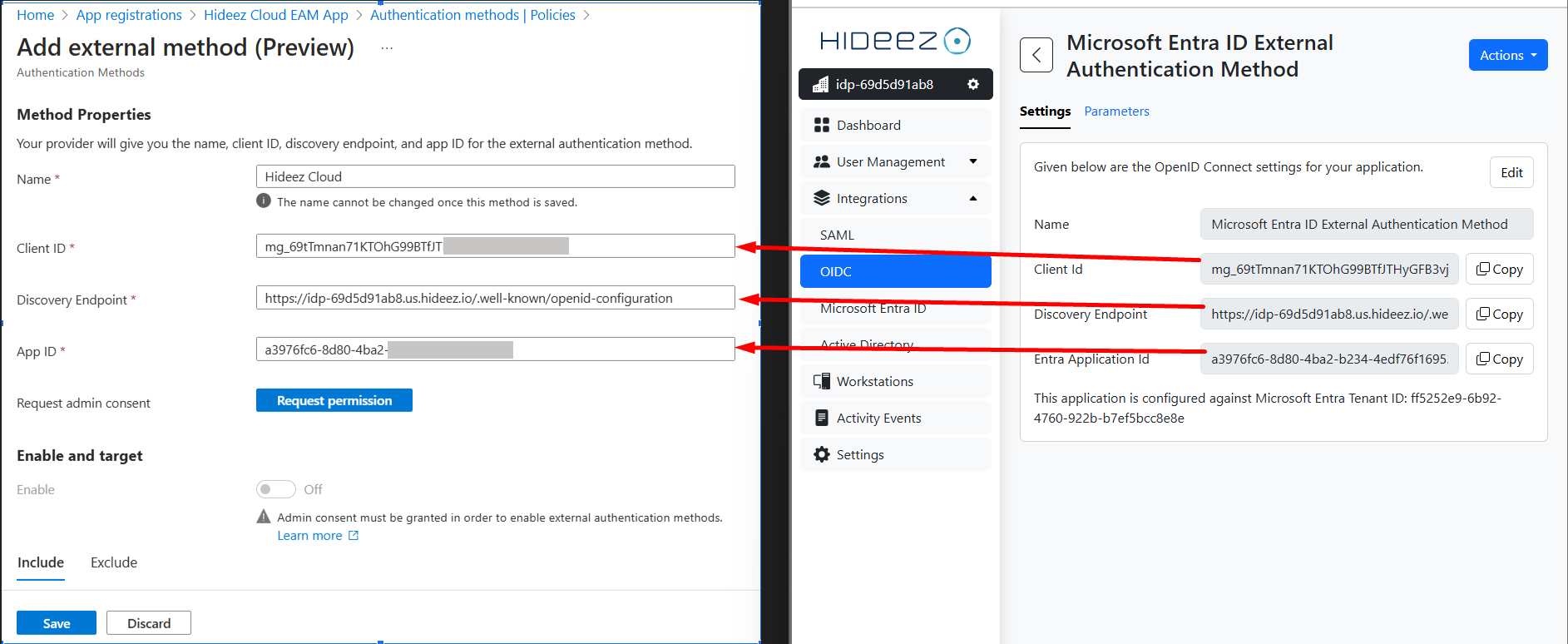
Click Request permission to grant admin consent for the app to read user information.
Click Enable.
Review the Included and Excluded Targets (all users are included by default).
Click Save.
Step 4: Configure Conditional Access Policy in Entra ID (Optional)
During migration, administrators are advised to create parallel Conditional Access Policies to test new configurations with a subset of users. This ensures minimal disruption and allows admins to verify the functionality of the custom controls.
Login to Microsoft Entra admin center.
Navigate to Protection → Conditional Access → Policies.
Click + New Policy (or edit an existing policy).
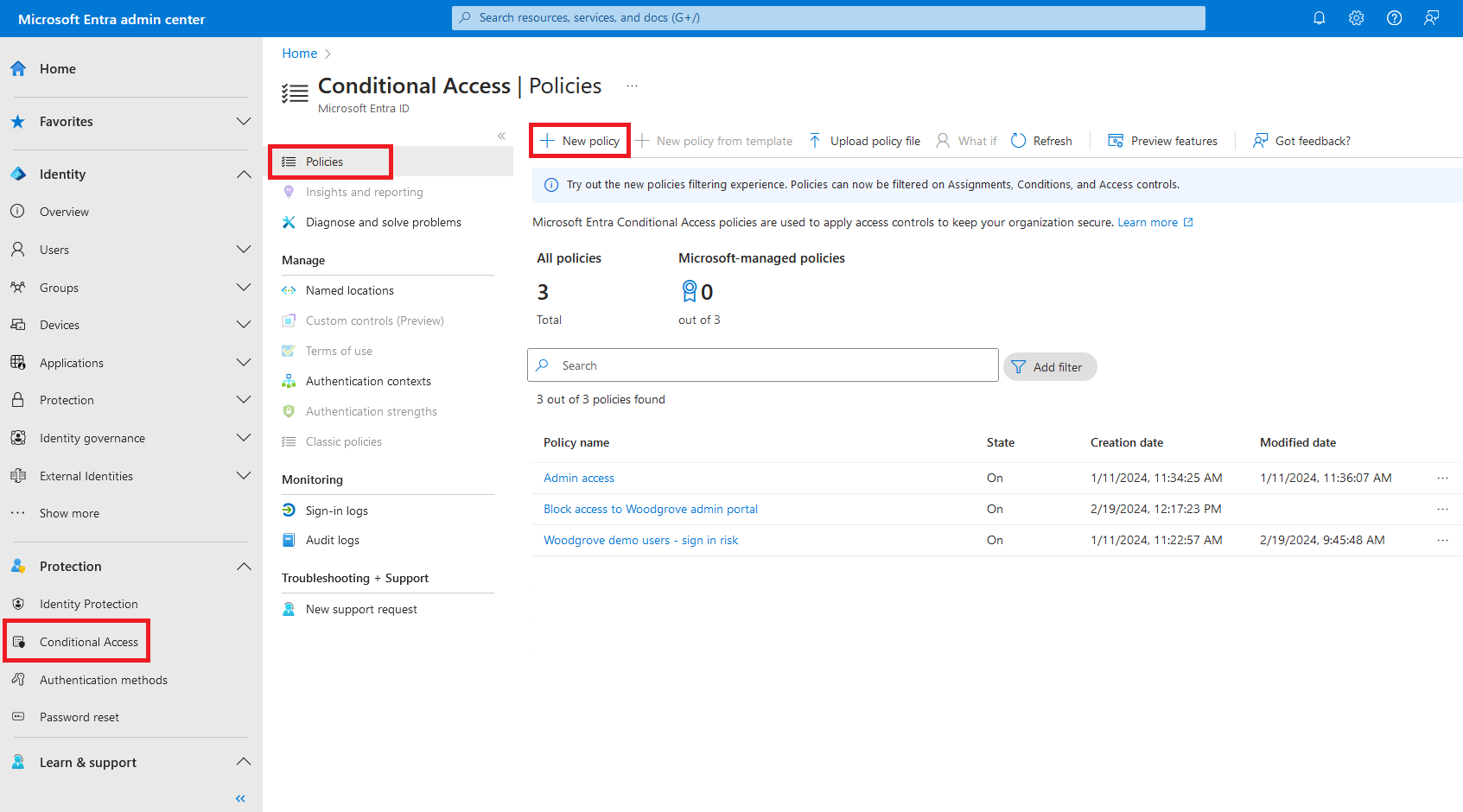
Configure the policy:
Specify Users: Define the users who will be affected by this policy.
Target Applications: Specify the applications covered by this policy.
Access Requirements:
Choose Require multifactor authentication so that the EAM (Hideez Cloud) is used as the MFA step.

Click on Save.
More information from more information from Microsoft can be found here Using Custom Control and EAM in parallel.
Last updated