WS-Federation
Hideez Identity Cloud - WS-Federation integration
What is WS-Federation:
WS-Federation is a web-based Single Sign-On (SSO) protocol designed by Microsoft to enable identity federation across different domains and applications.
Key Points:
Purpose: Allows users to authenticate to multiple systems or applications using a single set of credentials.
Claims-Based Authentication: Relies on claims to pass user identity and attributes between an Identity Provider (IDP) (e.g., AD FS) and a Relying Party (RP) (e.g., an application).
Microsoft-Centric: Primarily used with Microsoft services like AD FS, Exchange OWA, and SharePoint.
Simplified SSO: Enables seamless access to applications without repeated logins.
Message Format: Uses XML-based messages to transfer authentication tokens securely.
Compared to SAML: While SAML is widely used across platforms, WS-Federation is more commonly found in Microsoft ecosystems.
Example Flow:
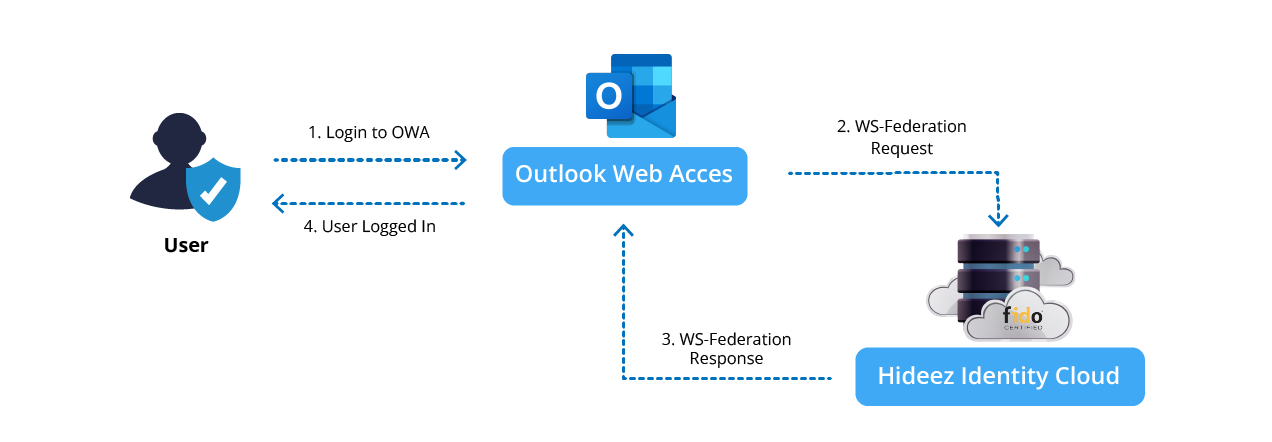
A user accesses Outlook on the Web (OWA) (Service Provider).
Outlook on the Web (OWA) redirects the authentication request to Hideez Identity Cloud (IDP).
Hideez Identity Cloud uses WS-Federation to authenticate the user and send a security token back to OWA.
The user gains access to OWA without entering credentials again.
Configure login to Exchange OWA directly via Hideez Identity Cloud as the Identity Provider using the SAML 2.0 protocol (2-tier architecture: Exchange OWA → SAML 2.0 → Hideez Identity Cloud).
Advantages:
No AD FS required: Eliminates the need for setting up and maintaining AD FS, simplifying the architecture, and reducing maintenance costs.
Simpler configuration: Without the additional AD FS component, the setup process is quicker and easier.
Faster access to resources: Direct integration with Hideez Identity Cloud reduces additional steps in the authentication process, providing quicker access to resources.
Reduced latency: The direct integration model may lower response times compared to a multi-step architecture involving AD FS.
Easier scalability: Scaling is simpler, as there’s no need to manage or expand an AD FS infrastructure for new integrations.
For more details, refer to the official Microsoft documentation on WS-Federation.
If you need assistance with server setup or configuring SAML/OIDC, our support [email protected] team is also available to help. We’ll be happy to assist you!
Last updated