GitHub Enterprise
Hideez Identity Cloud - Configuration SAML 2.0 for GitHub Enterprise
How to Configure SAML 2.0 for GitHub Enterprise
SAML single sign-on (SSO) gives organization owners and enterprise owners using GitHub Enterprise Cloud a way to control and secure access to organization resources like repositories, issues, and pull requests. Organization owners can invite your personal account on GitHub to join their organization that uses SAML SSO, which allows you to contribute to the organization and retain your existing identity and contributions on GitHub. If you're a member of an enterprise with managed users, you will instead use a new account that is provisioned for you and controlled by your enterprise.
Prerequisites
Access to the GitHub Enterprise admin account.
Administrative access to Hideez Identity Cloud to configure the IDP.
A configured Hideez Identity Cloud instance with user identities set up.
The users exist in Hideez Identity Cloud.
The user is added to the GitHub organization.
Step 0: Add users to the Hideez Identity Cloud
You have to add the users that belong to GitHub Enterprise to the tenant on Hideez Identity Cloud.
Please follow this guide to add the user:
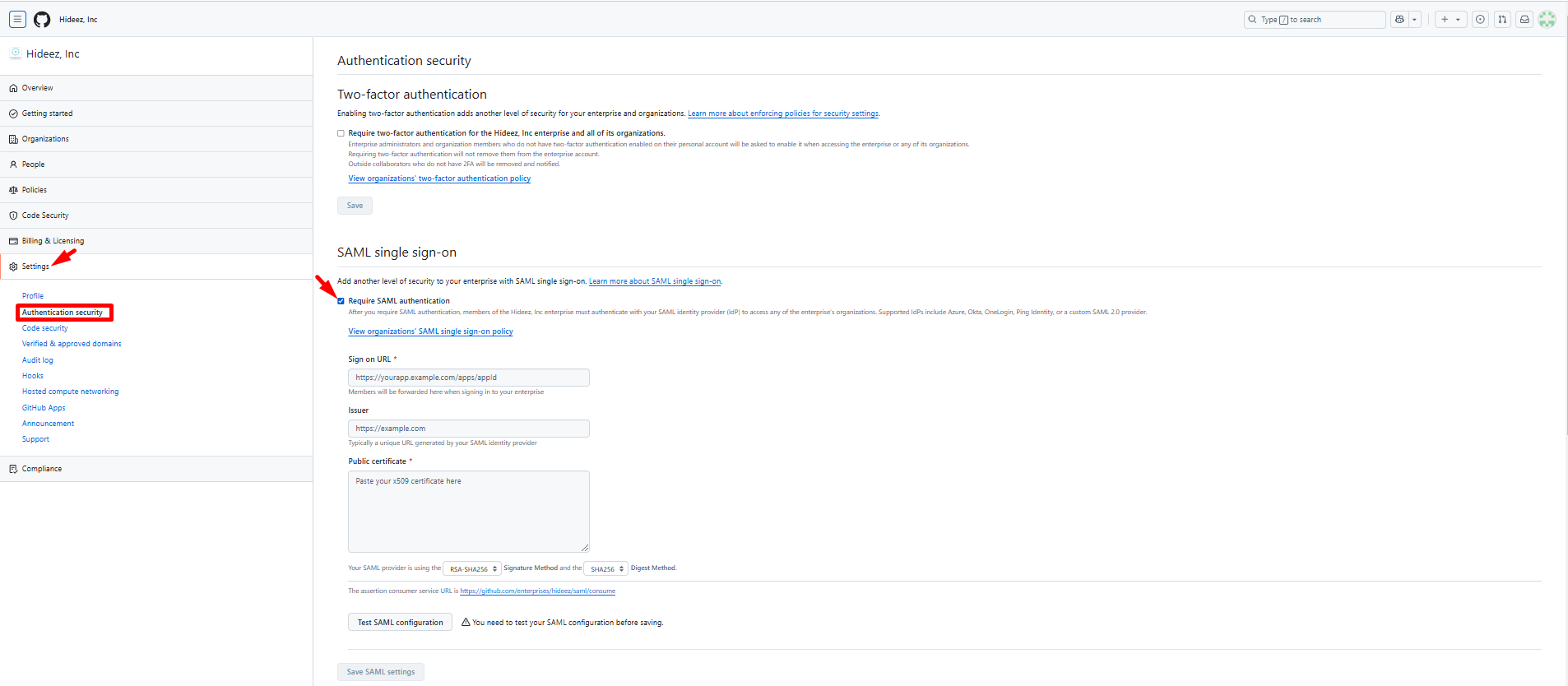
Step 1: Enable SAML Single Sign-On in GitHub Enterprise
Log in to your GitHub Enterprise account as an admin.
Navigate to the organization or enterprise settings:
For organizations: Go to Settings → Security.
For enterprise accounts: Go to Enterprise settings → Authentication.
In the "SAML single sign-on" section, click Enable SAML authentication.
Step 2: Configure the SAML Settings in Hideez Identity Cloud
General Application Setup
Log in to your Hideez Identity Cloud admin portal.
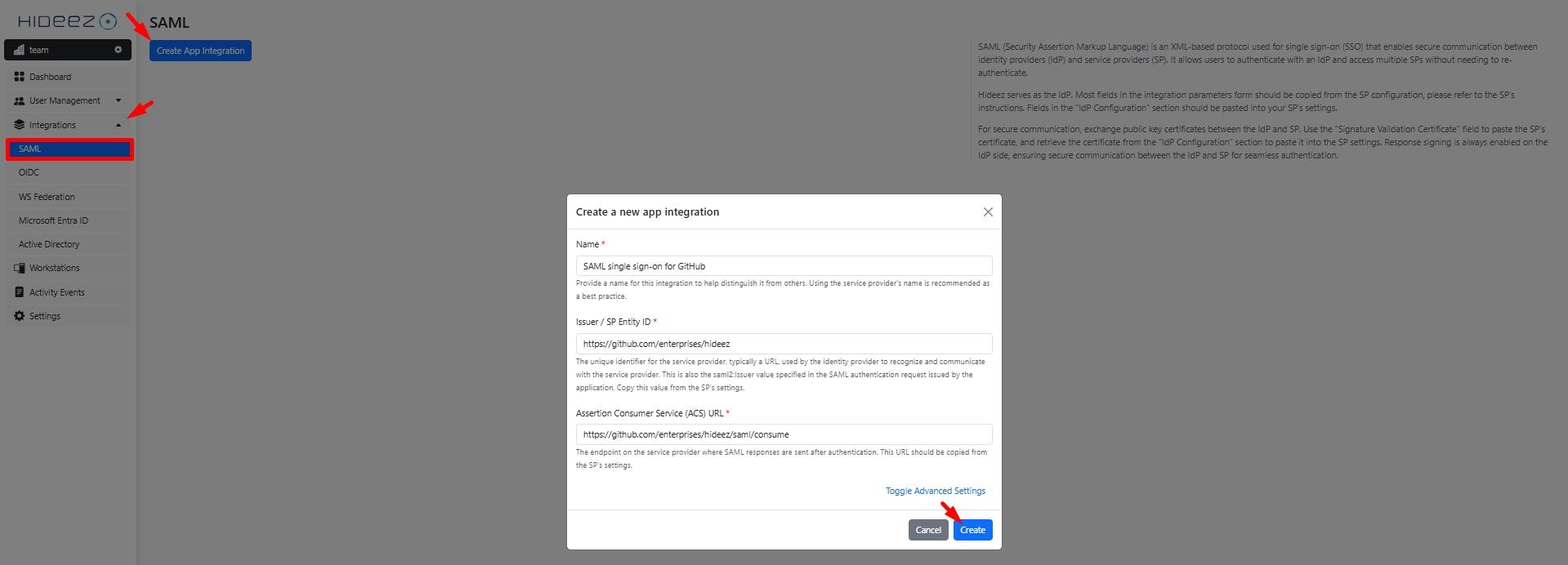
Go to Integrations→SAML and create a new SAML application for GitHub Enterprise.
Provide the following details during the setup:
Name: Familiar name (
e.g. SAML single sign-on for GitHub).Issuer / SP Entity ID:
https://github.com/enterprises/<organization-name>/(replace<organization-name>with your organization's name). In our case:https://github.com/enterprises/hideez.ACS URL (Assertion Consumer Service URL):
https://github.com/orgs/<organization-name>/saml/consume. In our case:https://github.com/enterprises/hideez/saml/consume.
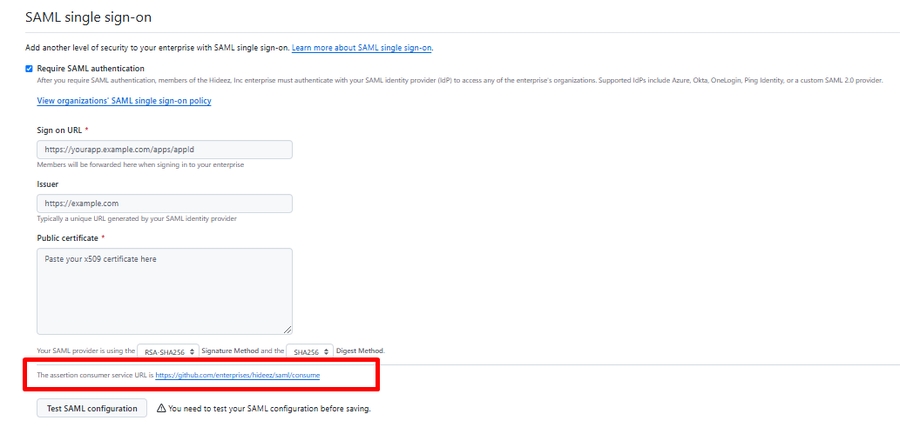
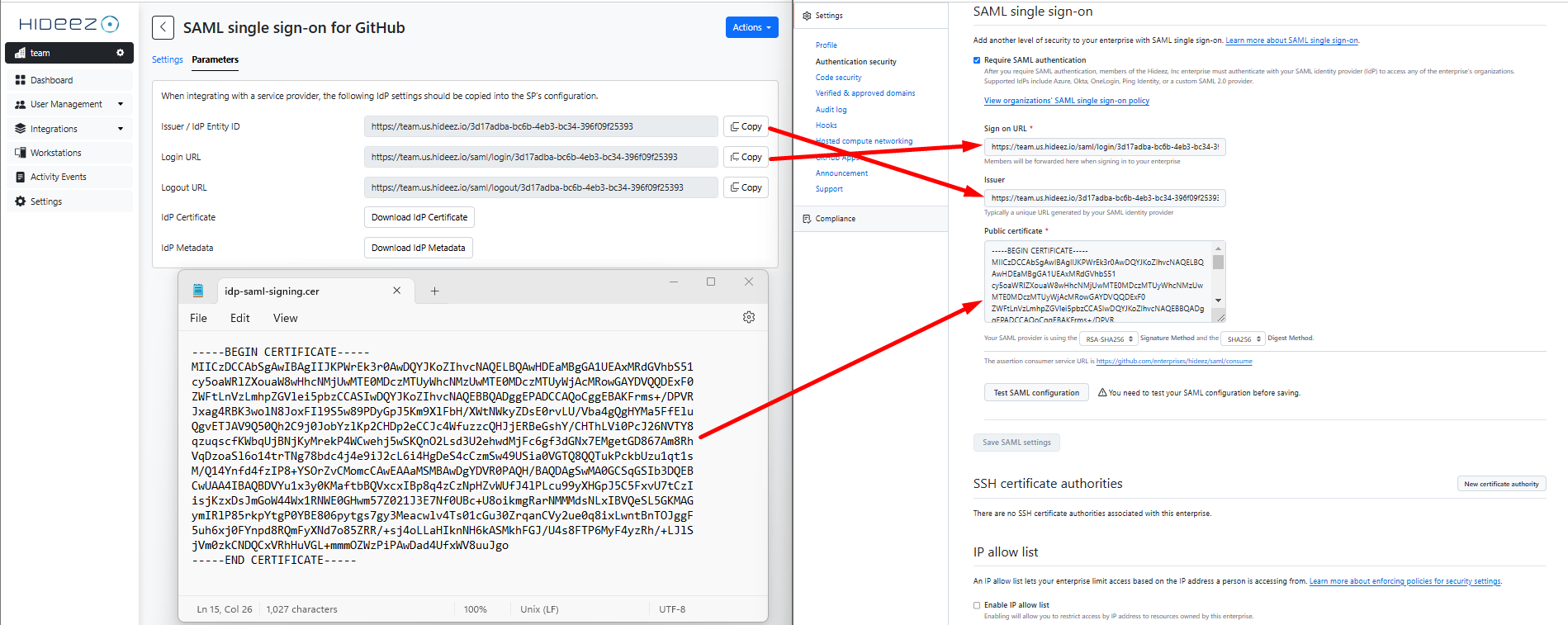
You can find the assertion consumer service URL directly on your GitHub Enterprise account:
Click Create.
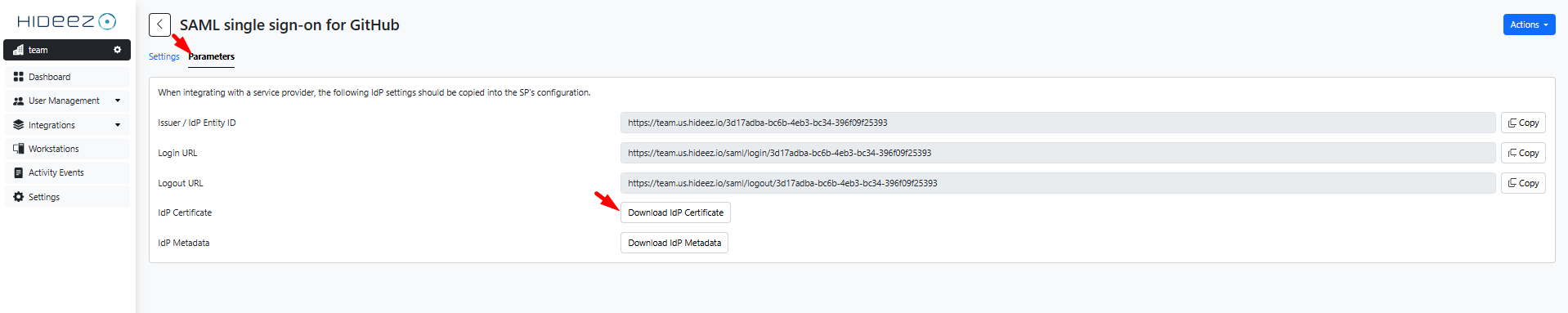
Go to the Parameters tab and keep it open. We will use it later on.
Download the Hideez Identity Cloud signing certificate (in X.509 format).
Step 3: Complete SAML Setup in GitHub Enterprise
Return to the GitHub Enterprise SAML settings page.
Provide the following details:
Sign on URL: The SSO URL from Hideez Identity Cloud.
Issuer: The Entity ID or Issuer from Hideez Identity Cloud.
Public Certificate: Paste the X.509 certificate downloaded from Hideez Identity Cloud.
You can open the Public Certificate downloaded from Hideez Identity Cloud on your computer, copy it, and paste it to GitHub.
Step 4: Test the SAML Configuration
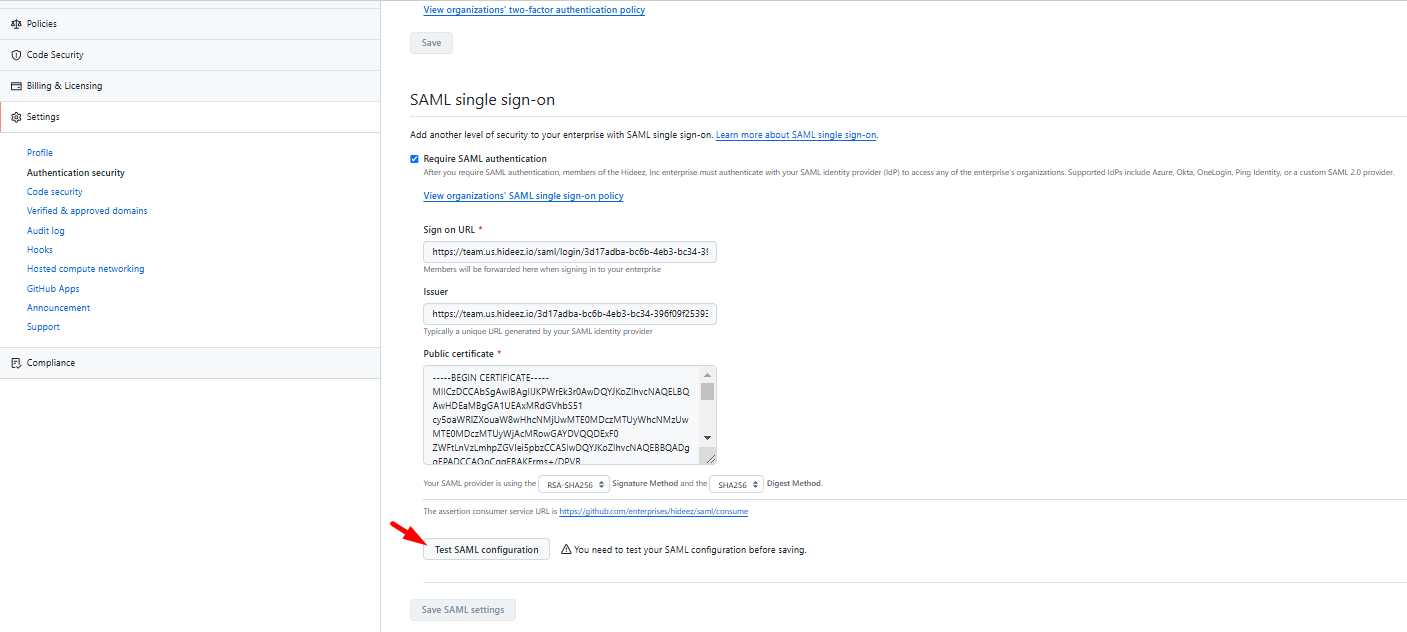
On the GitHub Enterprise SAML settings page, click Test SAML login.
Verify that you are redirected to Hideez Identity Cloud for authentication.
Complete the login process and confirm access to GitHub Enterprise.
Click Test SAML configuration before saving settings and test SAML login to your GitHub Enterprise account using Hideez Identity Cloud.
Step 5: Save SAML for the GitHub Enterprises
After testing is successful, return to the SAML settings page.
Click Enforce SAML single sign-on.
Confirm the enforcement to require SAML authentication for all members.
For further assistance, refer to GitHub Enterprise documentation and Hideez Identity Cloud support resources.
If you need assistance with server setup or configuring SAML/OIDC, our support [email protected] team is also available to help. We’ll be happy to assist you!
Last updated