Google Workspace
Hideez Identity Cloud - Configuration SAML 2.0 for Google Workspace
How to Configure SAML 2.0 for Google Workspace
1. Create a User Group or Organizational Unit (OU):
Define a user group, OU, or select individual users to whom Google Workspace access via Hideez Cloud SAML SSO will apply:
Go to admin.google.com.
Navigate to Menu → Directory → select User, Group, or Organizational Unit (OU).
Choose an existing option or create a new group, user, or OU for SAML login via Hideez Cloud.
User: An individual Google Workspace account assigned to a specific person, capable of being grouped in OUs and Groups.
Organizational Unit (OU): A structured way to organize users by department or role, allowing administrators to apply distinct settings and policies (e.g., security and app access) to specific groups.
Group: A collection of users for communication (e.g., email lists) and shared resource access (e.g., Drive files). Groups support multiple users without a hierarchical structure.
Example: Applying SAML Login to a User Group
Navigate to Menu → Directory → Group and create group.
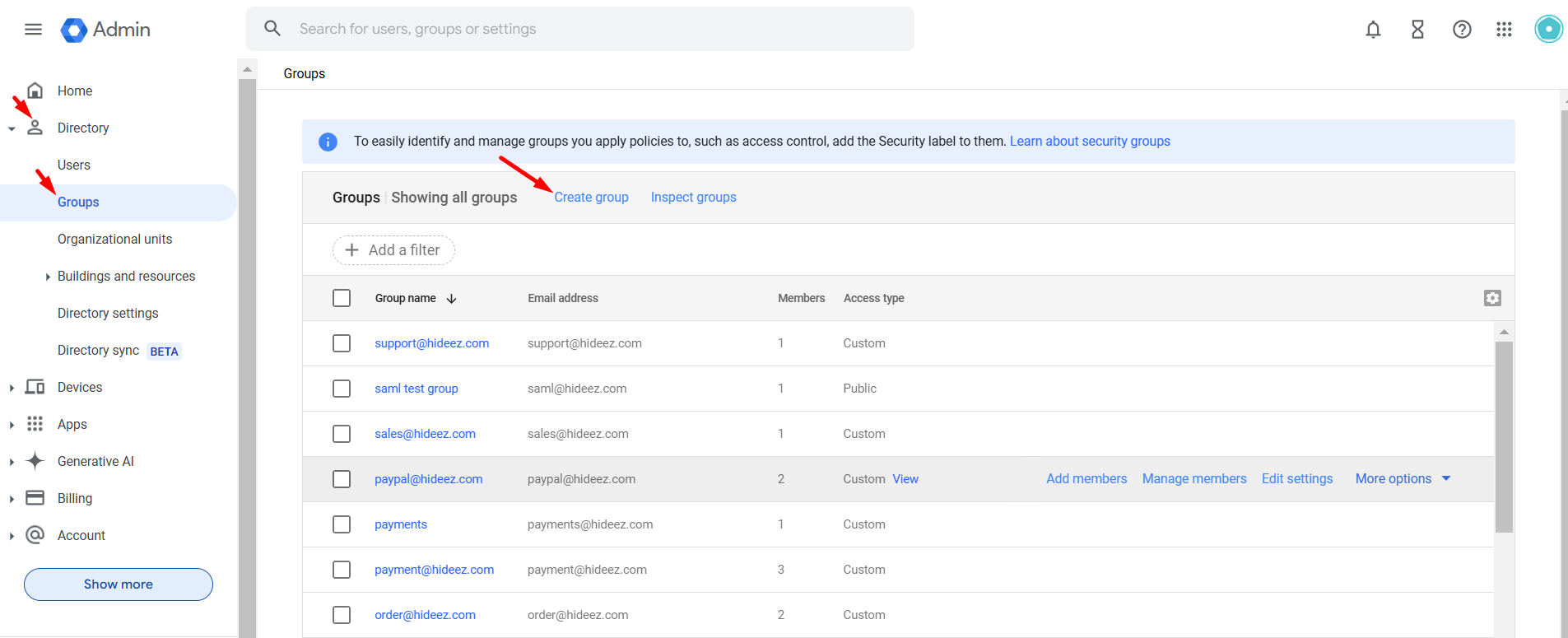
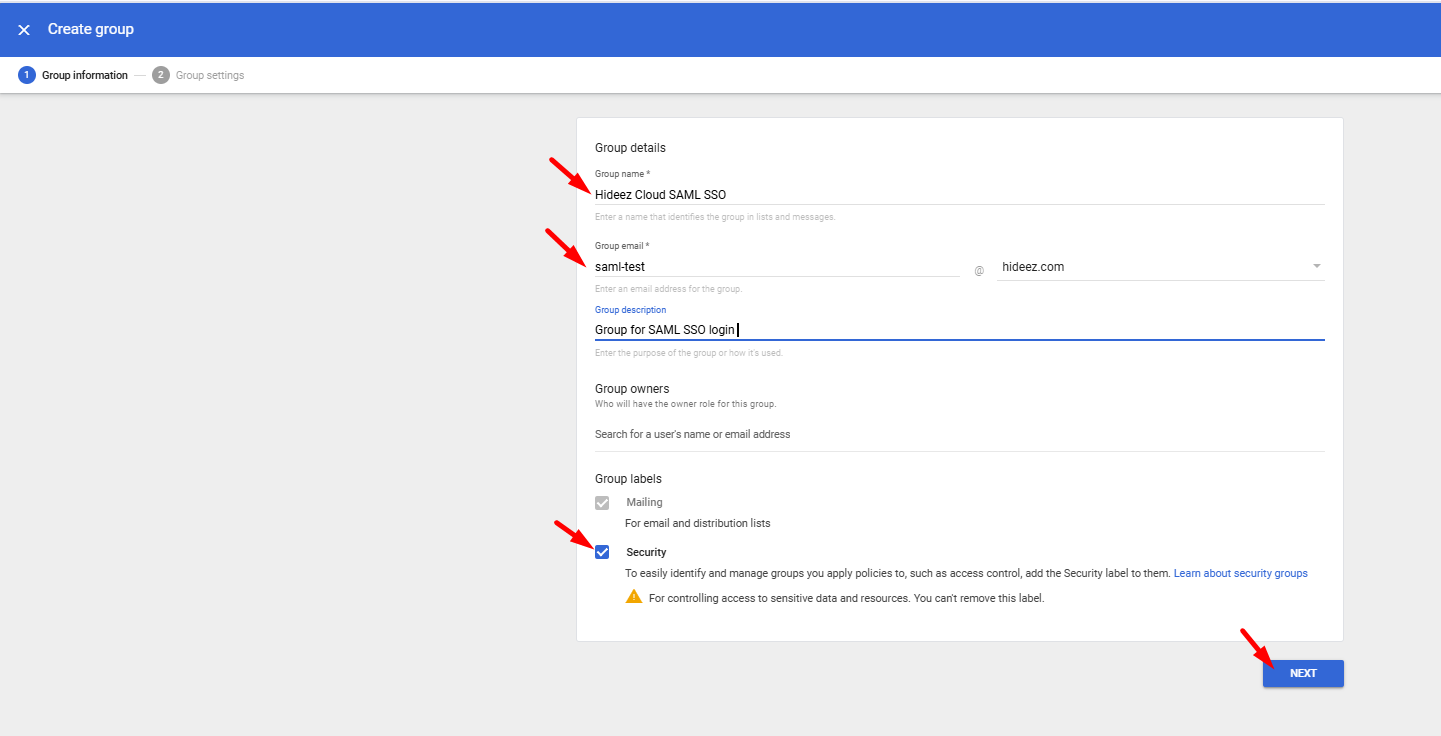
Enter required group details:
Group name
Group email (existing or new email for the group)
Select Group labels → Security, and proceed to configure Access type (e.g., Public), then click Create Group.
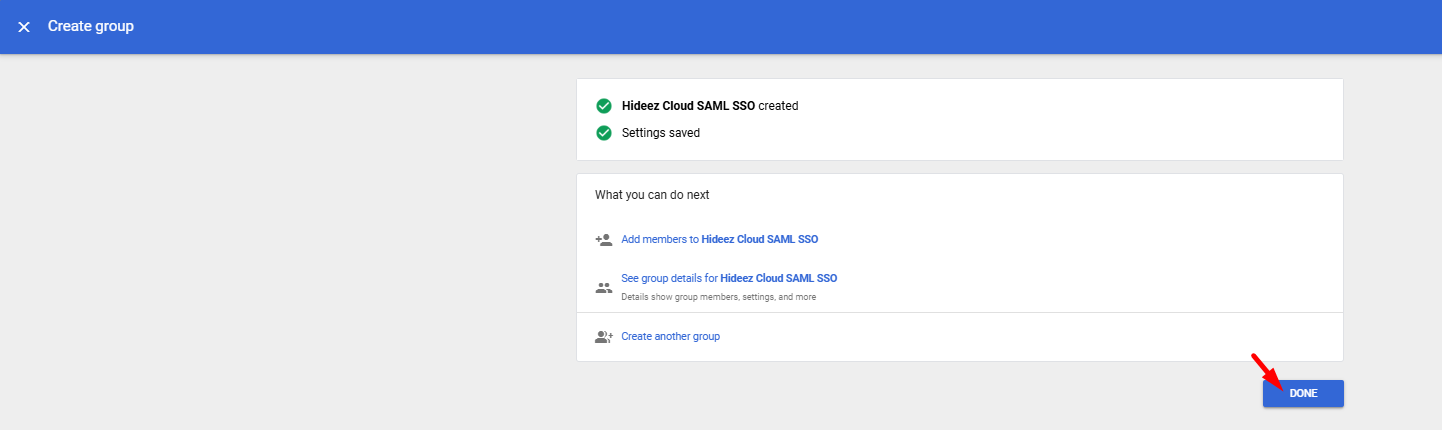
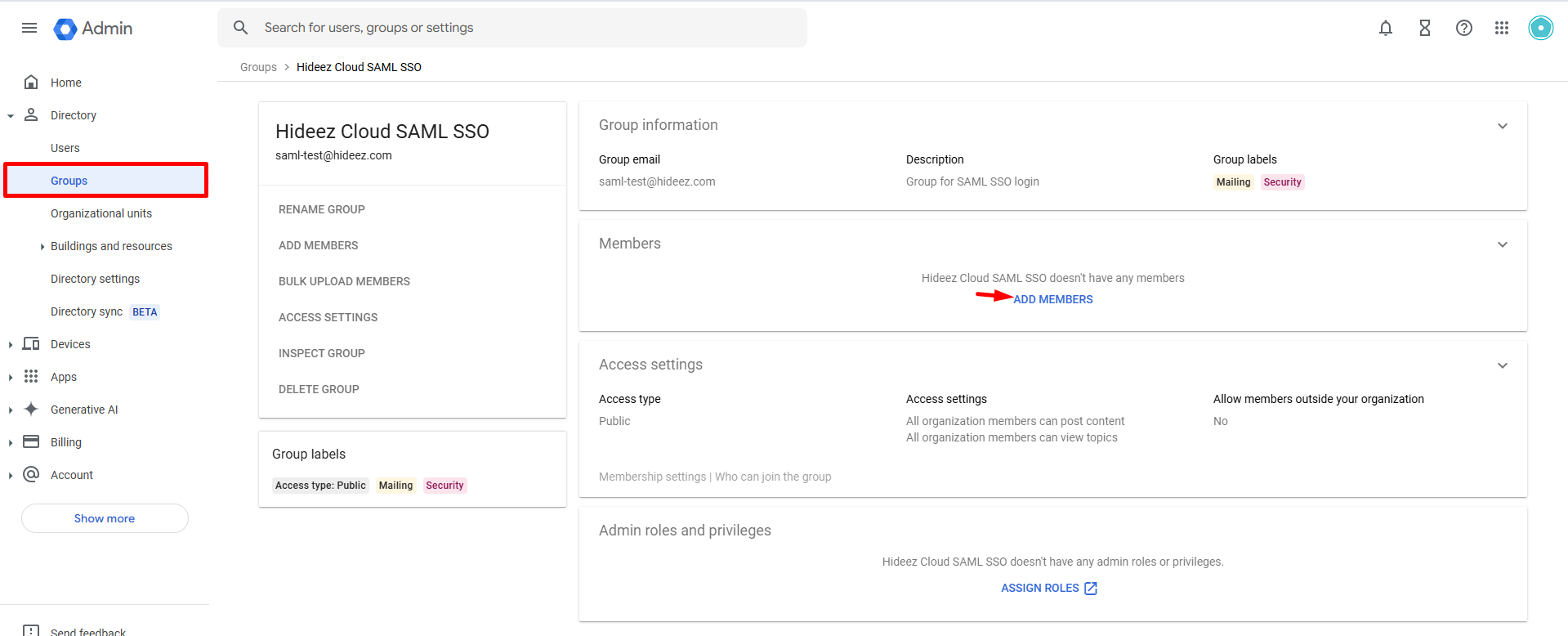
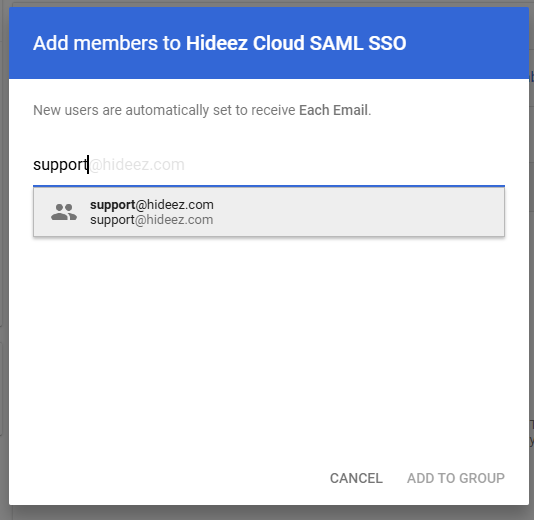
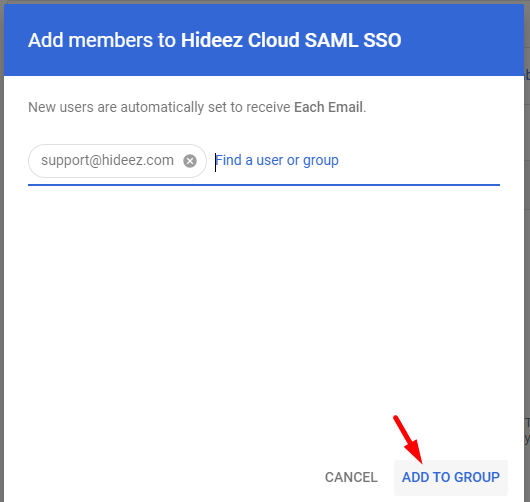
2. Add Users to the Group for SAML Login Access
Select the newly created group and add users who will access Google services via SAML through Hideez Identity Cloud.
3. Access Google Admin Console for SAML Setup
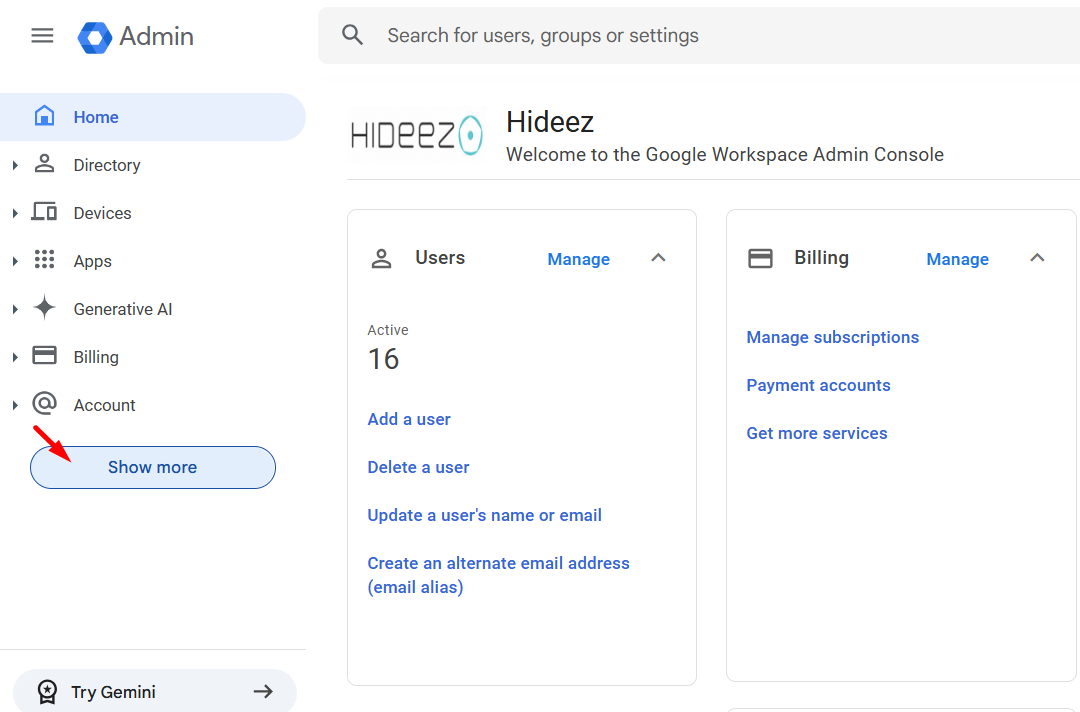
In admin.google.com.
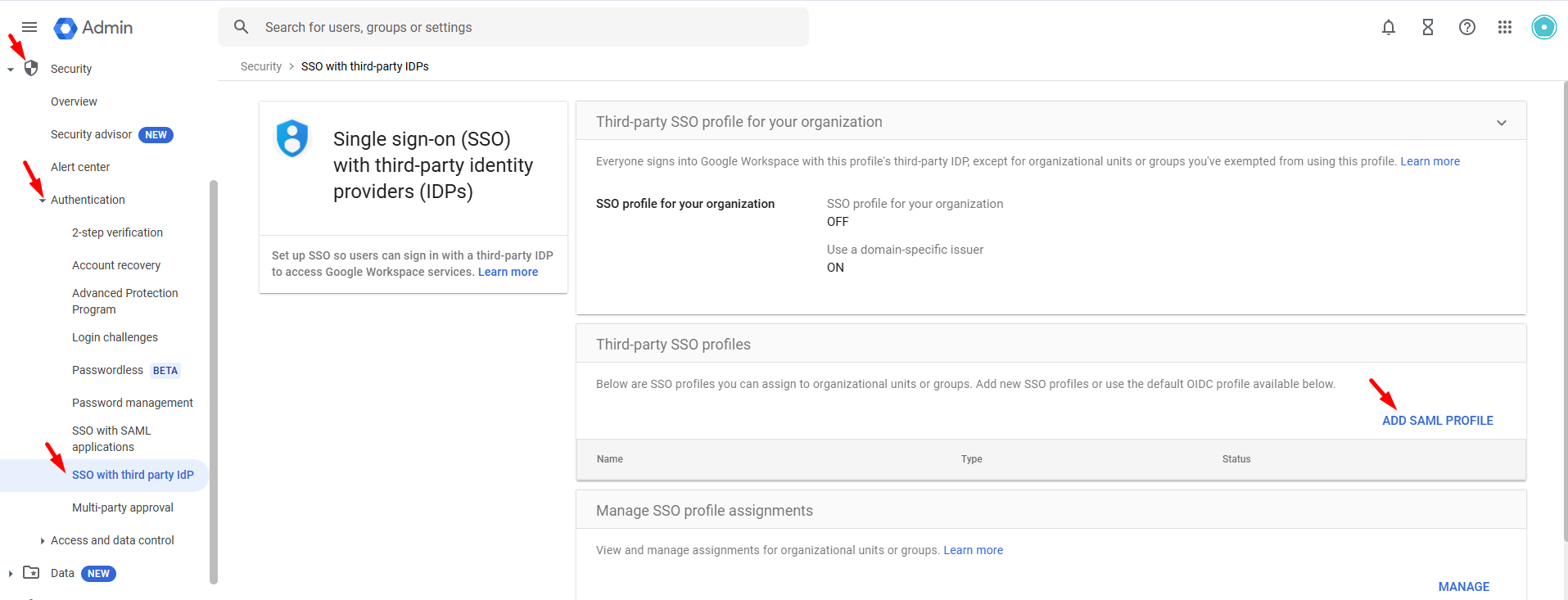
Navigate to Menu → Show more→Security → Authentication → SSO with third-party IdP.
Under Third-party SSO profiles, click Add SAML profile.
Enter a profile name (e.g., "Hideez Cloud") and save.
4. Create SAML App Integration in Hideez Cloud
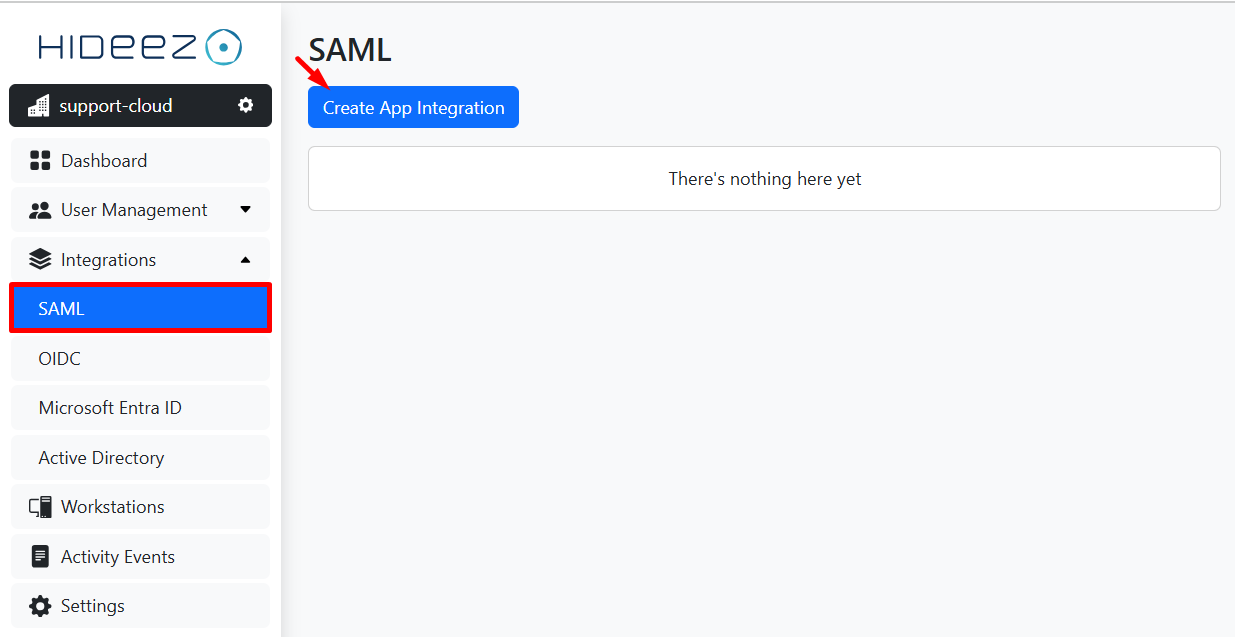
In Hideez Cloud, go to Integrations → SAML.
Click on Create App Integration and enter:
Name: (e.g., Google Multi-IDP SSO Profile).
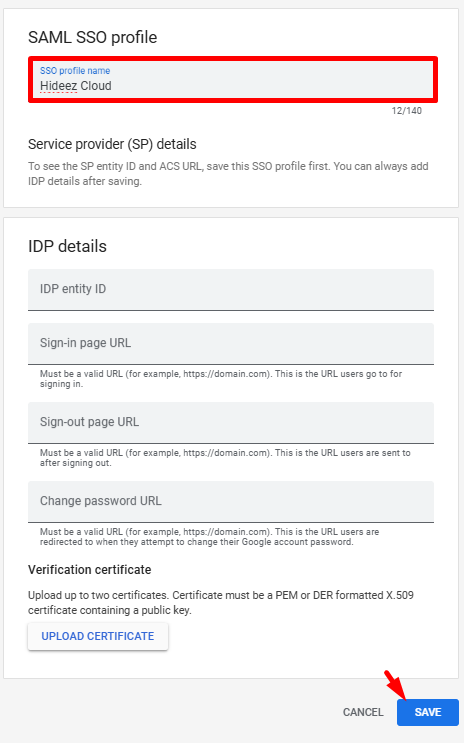
In Google Admin, open the SAML profile and copy the following details:
Issuer/SP Entity ID (e.g.,
https://accounts.google.com/samlrp/unique-id).ACS URL (e.g.,
https://accounts.google.com/samlrp/unique-id/acs).
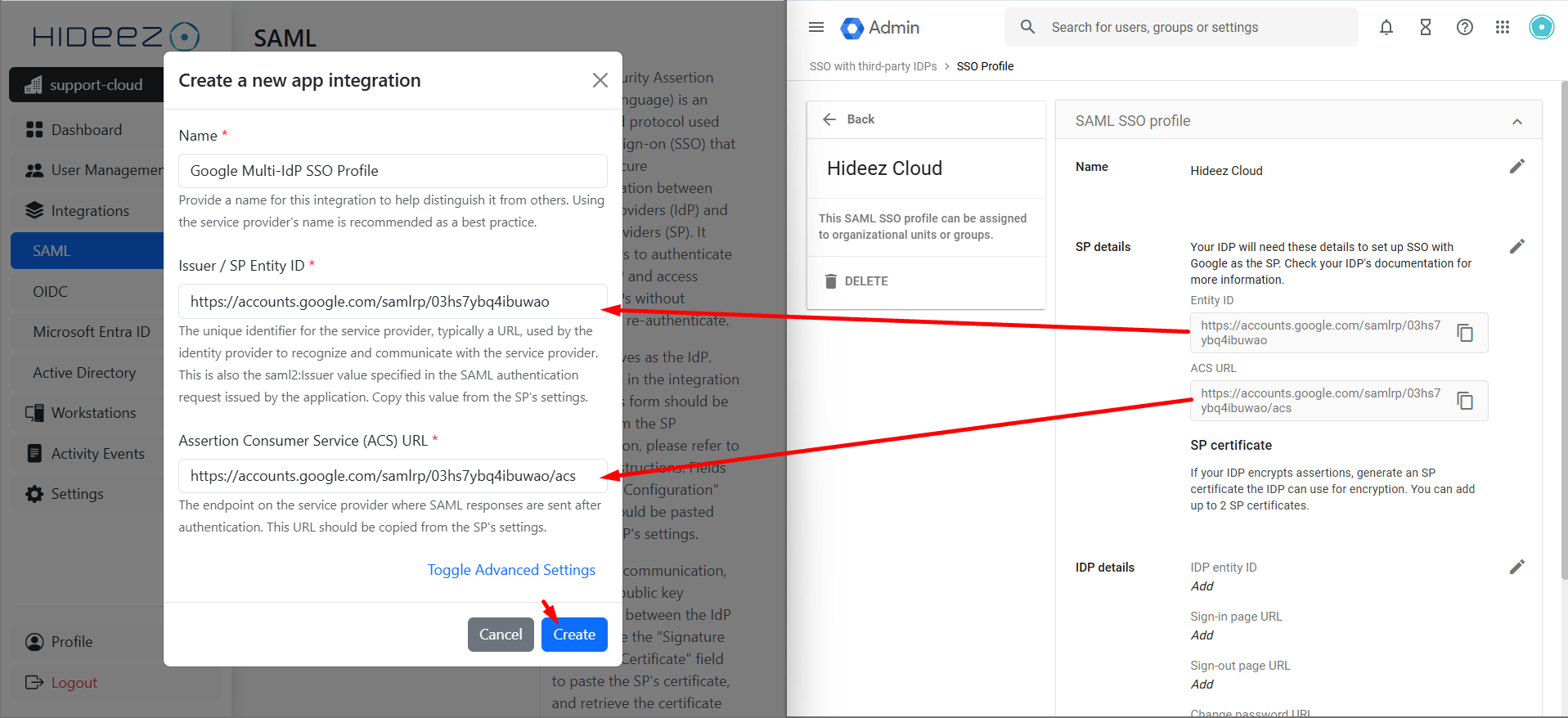
Click Create.
5. Complete the SAML Profile in Google Admin Console
In Google Admin, open the SAML profile and fill in IDP details from Hideez Cloud:
IDP entity ID
Sign-in page URL
Sign-out page URL (optional)
Verification certificate
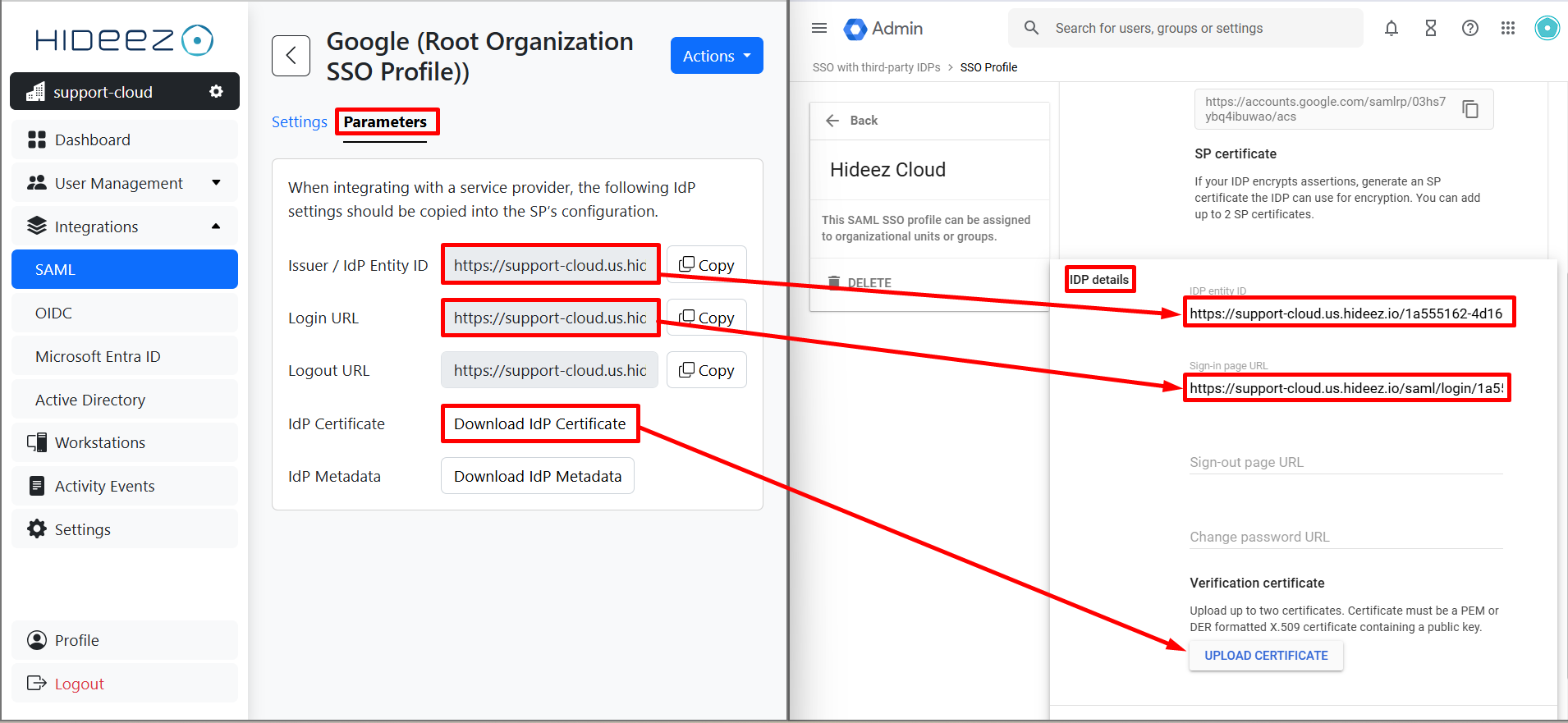
Note: The Logout URL in Hideez Cloud and the Sign-out Page URL in Google Workspace serve different purposes. You have two options for configuration:
Leave the field blank in Google Workspace: Upon logging out of Google Workspace, you will automatically be redirected to the initial email entry page.
Specify a tenant's name in the field: Example:
https://tenant_name.us.hideez.io(e.g.,https://support-cloud.us.hideez.io). In this case, logging out of Google Workspace will redirect you to the Hideez Cloud End-User Dashboard.
Click Save.
6. Assign SSO Profiles for Group
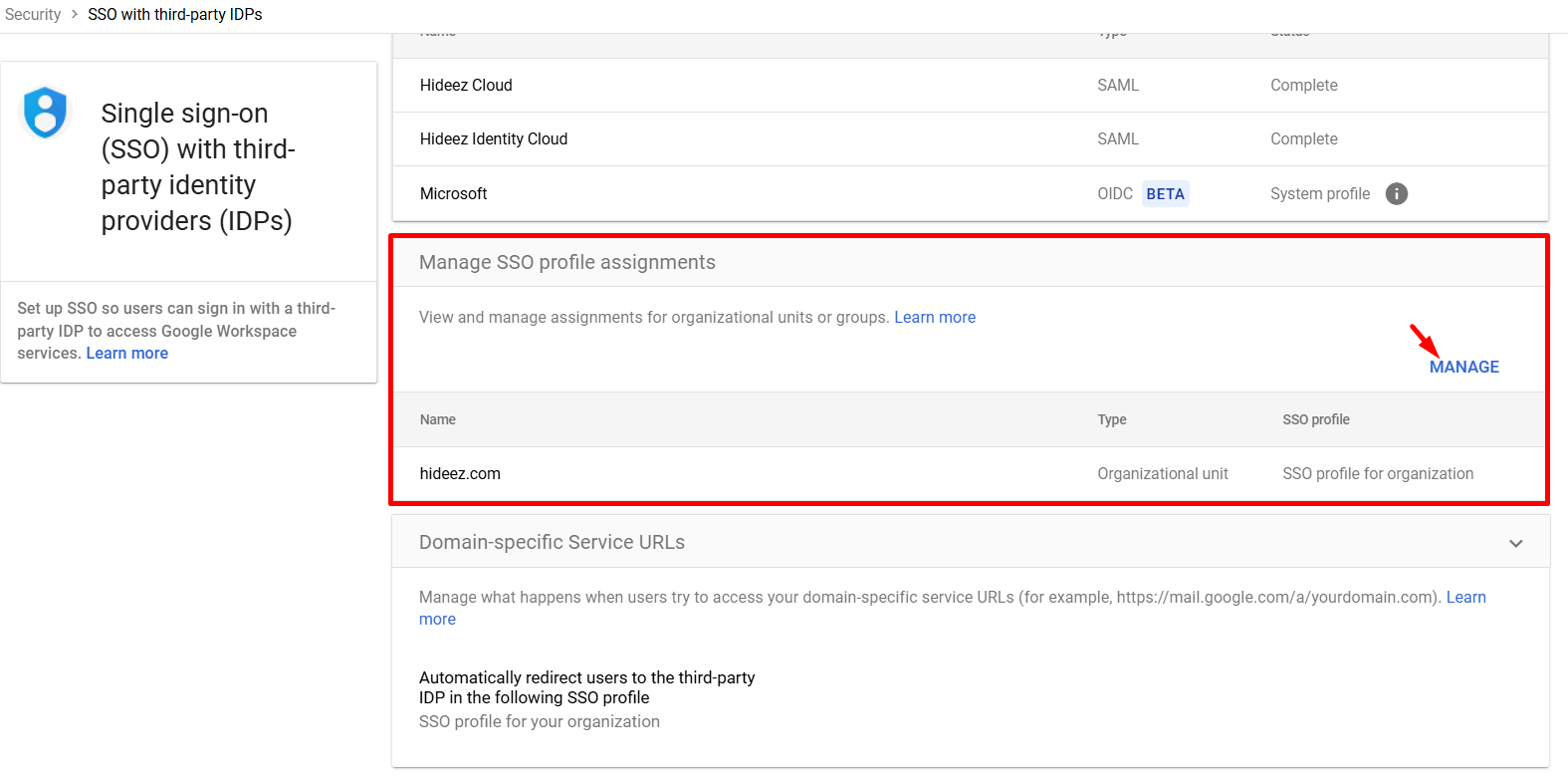
Go to Manage SSO profile assignments in Google Admin Console.
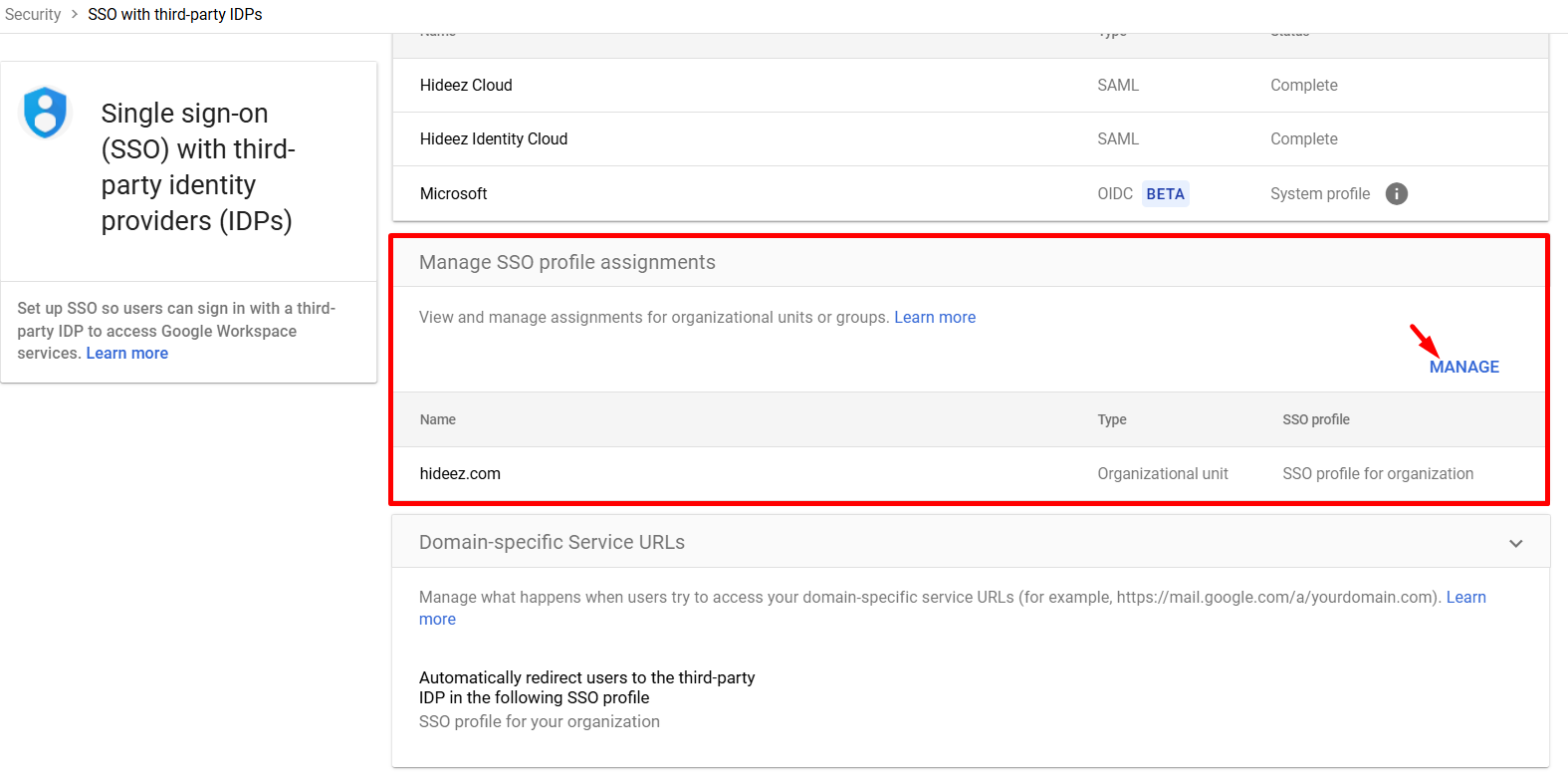
Assign the new SSO profile to specific OUs or groups as needed.
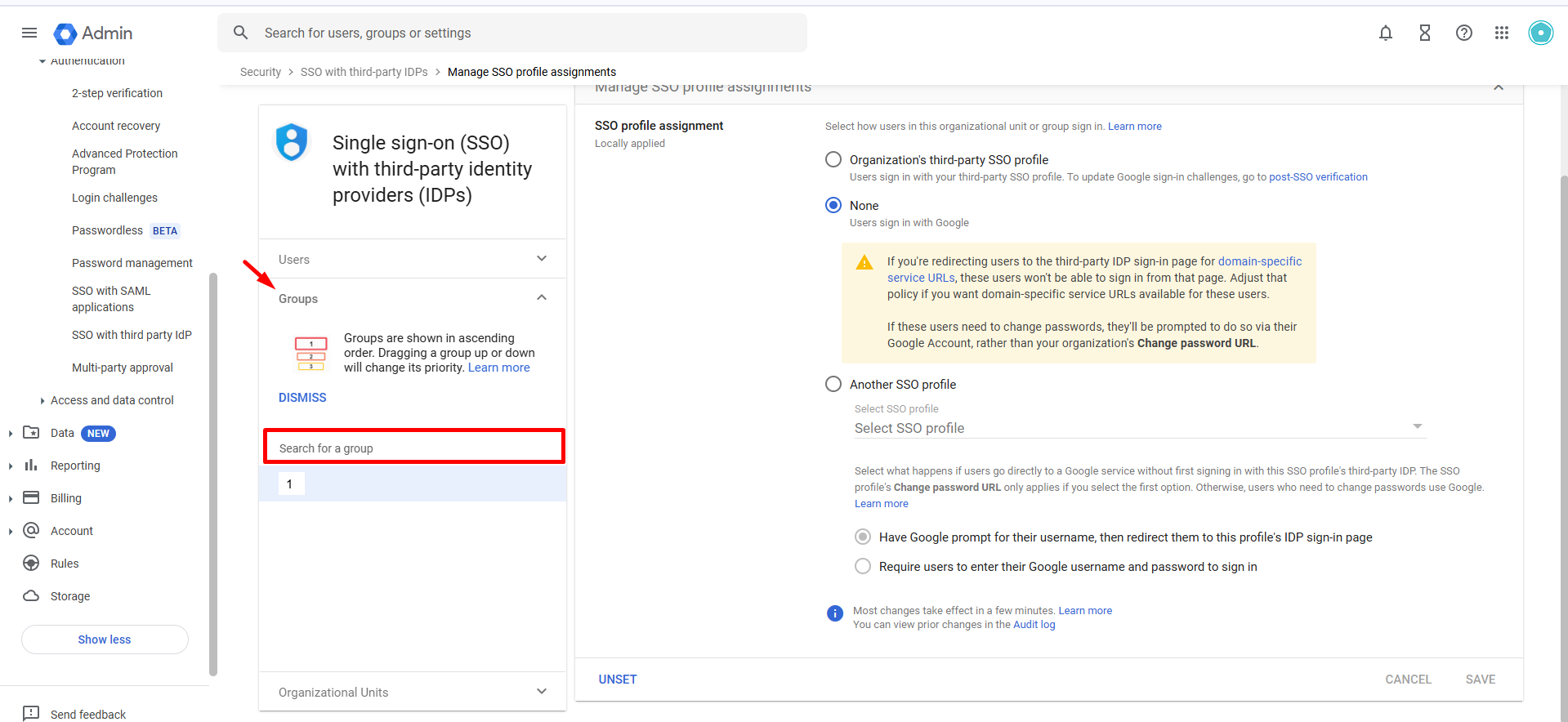
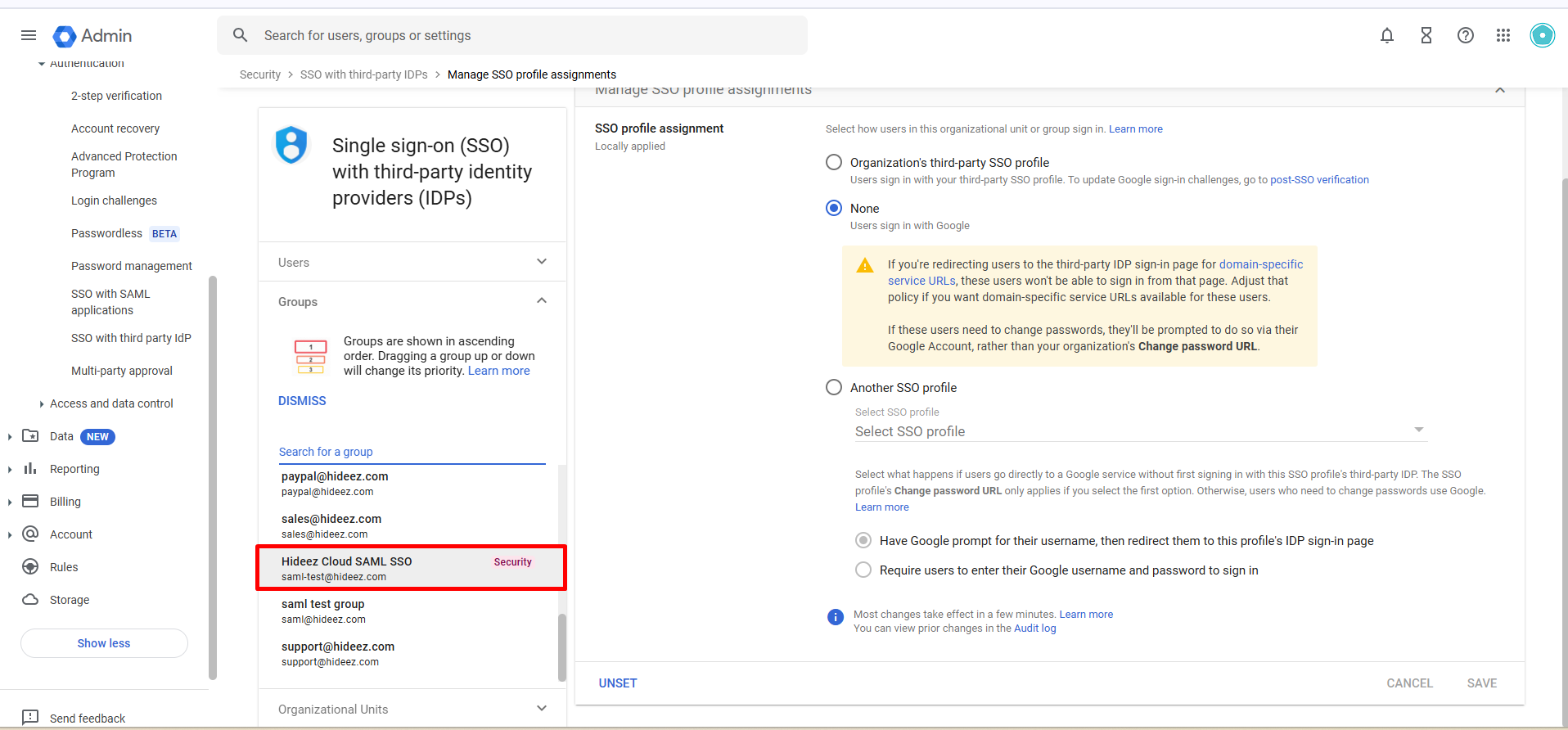
Click Save.
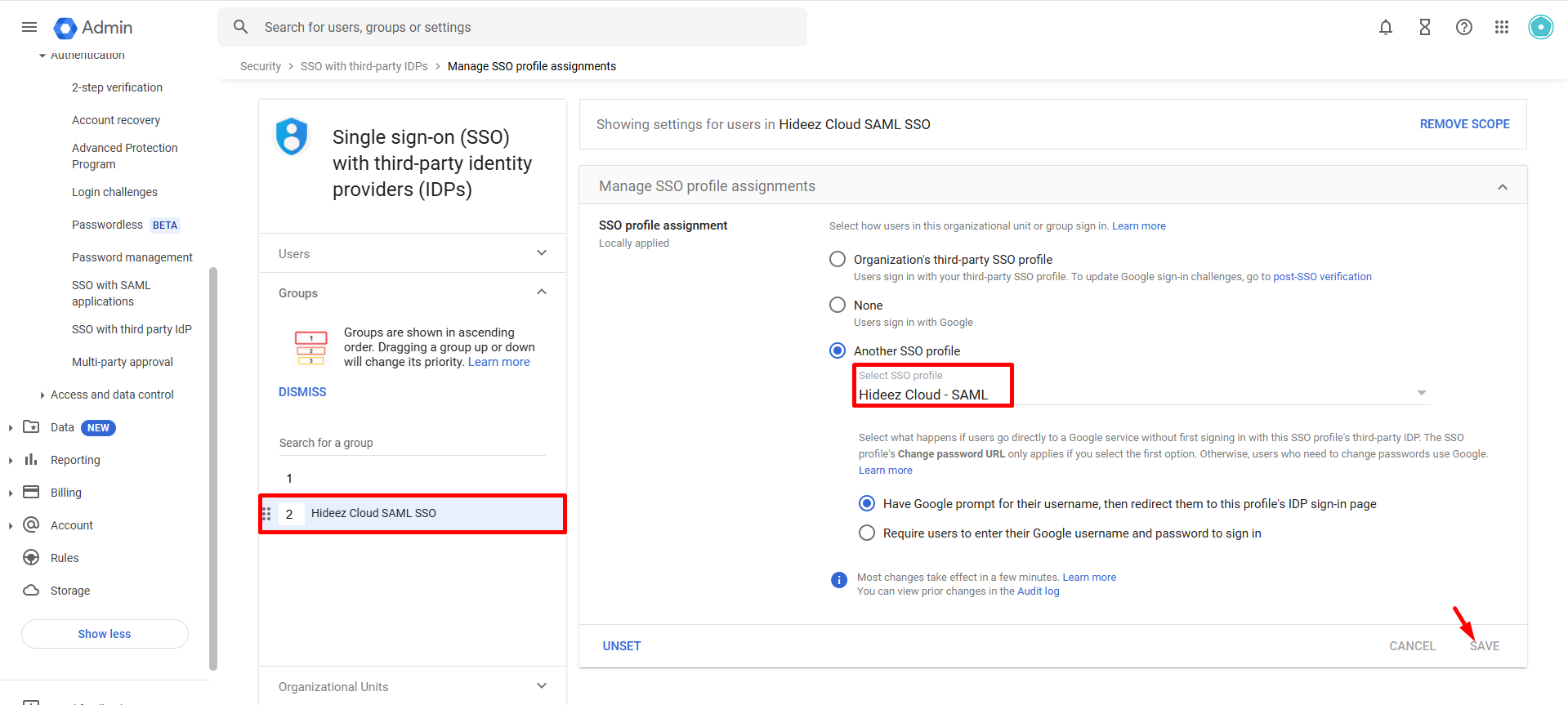
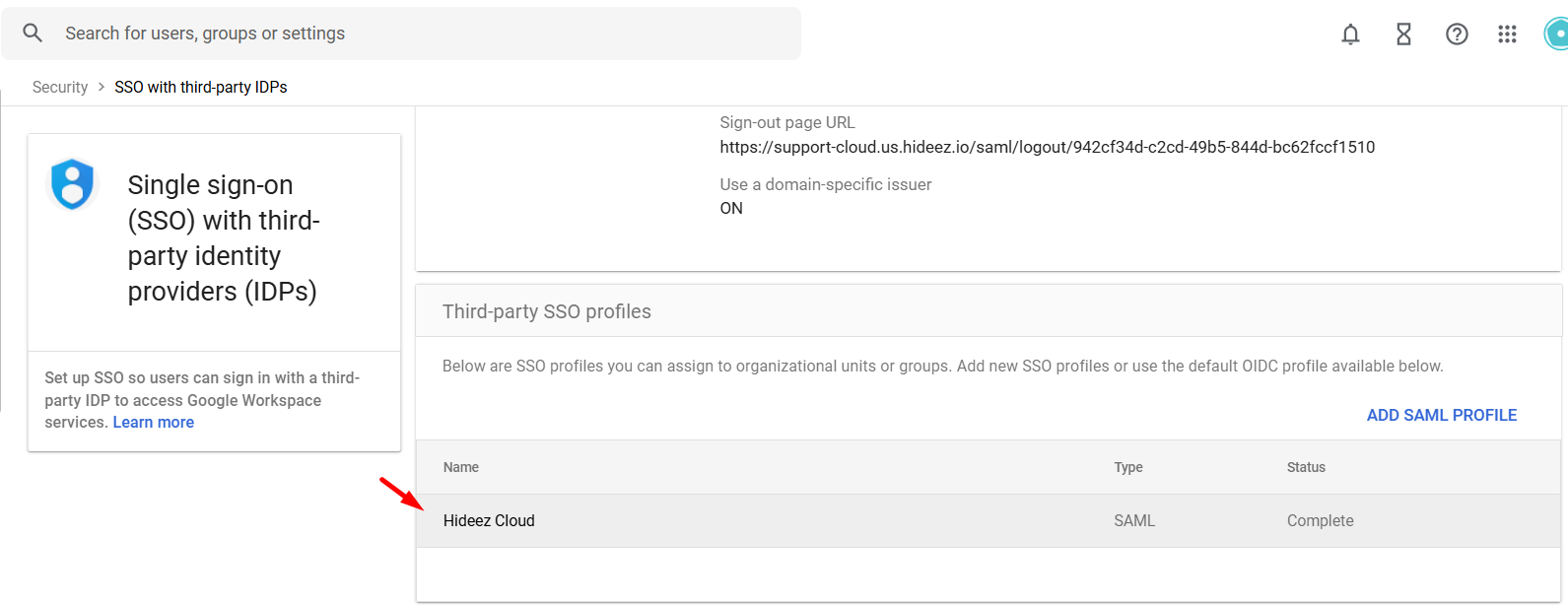
Ensure the profile created in Step 3 has a status of "Complete"; otherwise, it will not appear in the Another SSO profile selection.
Logging into Google Services via Hideez Identity Cloud Users can log in to Google services (e.g., Drive, Gmail) through Hideez Identity Cloud, with options such as:
Passwordless login with Passkey or Hideez Authenticator App.
Standard login with a second authentication factor (TOTP).
SP-Initiated SSO Links for Google Services These URLs allow direct access to services through SSO:
Mail:
https://www.google.com/a/your-domain.com/ServiceLogin?continue=https://mail.google.comDrive:
https://www.google.com/a/your-domain.com/ServiceLogin?continue=https://drive.google.comCalendar:
https://www.google.com/a/your-domain.com/ServiceLogin?continue=https://calendar.google.comReplace
your-domain.comwith your actual domain.
Summary for Option 2: Multi-IDP SSO Profile
Create a user group and add members.
Set up a SAML profile in Google Admin and Hideez Cloud.
Assign the profile to the specific group.
Save all changes.
Disable Google Workspace Login via Hideez Cloud SAML
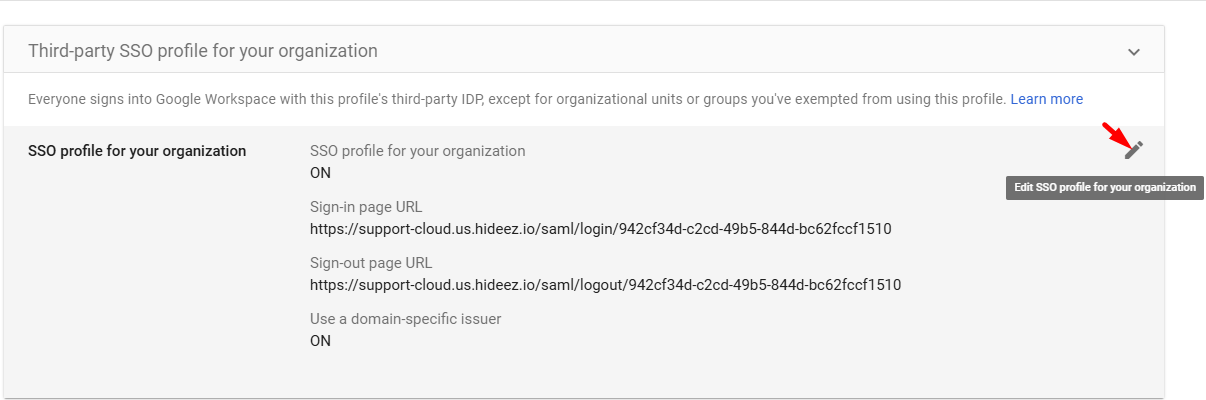
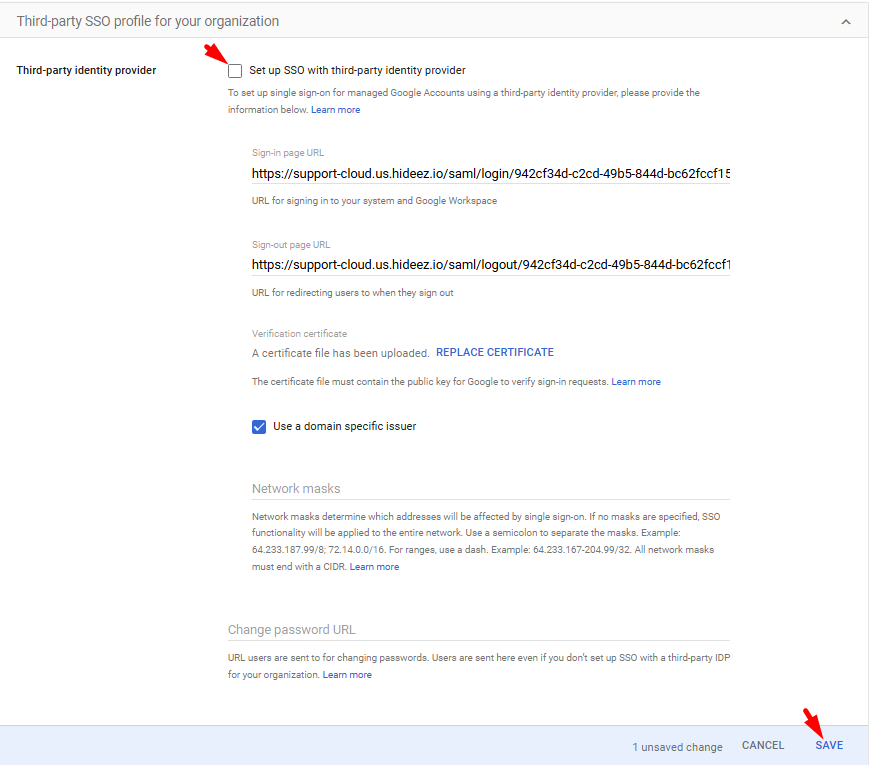
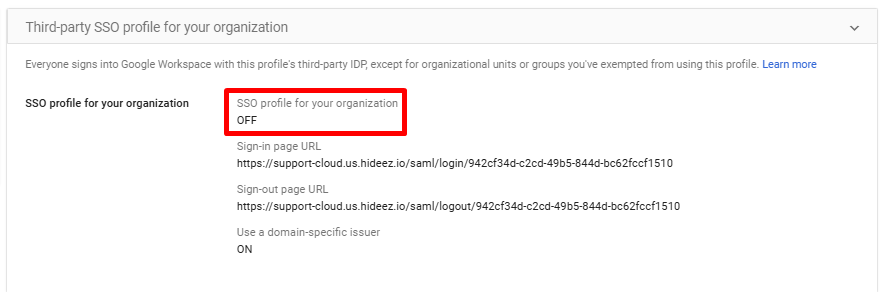
Root Organization SSO Profile: Uncheck Set up SSO with third-party identity provider in Google Admin Console and save.
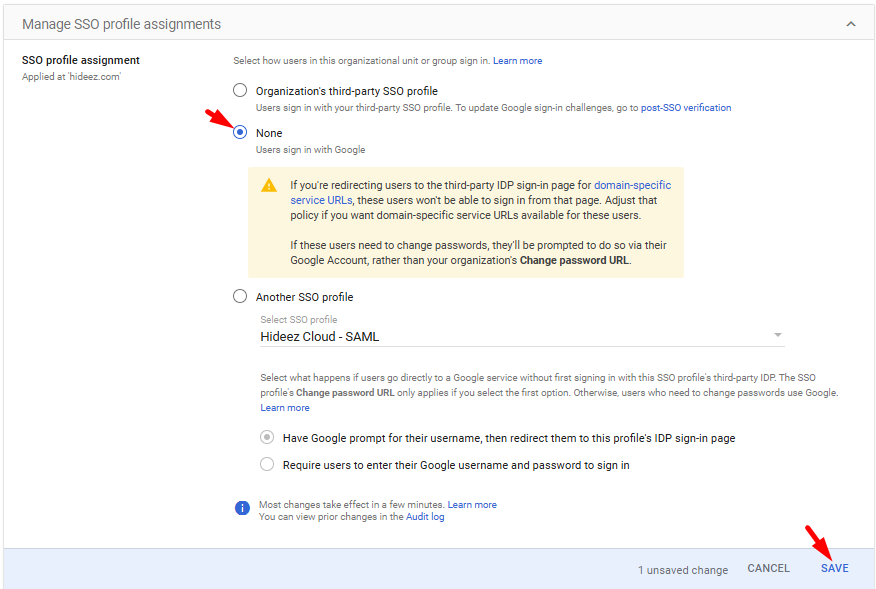
Multi-IDP SSO Profile: Go to Manage SSO profile assignments → select None for SSO profile and save.
If you need assistance with server setup or configuring SAML/OIDC, our support [email protected] team is also available to help. We’ll be happy to assist you!
Last updated