Setting Up Workstation Passwordless Logon Settings on Hideez Identity Cloud
1. The first parameter (Cryptographic Service Provider Name) must be set to:
Microsoft Base Smart Card Crypto Provider2. The second parameter (Certificate Config) is the name of the domain controller and the name of the certification authority:
certutil -config - -ping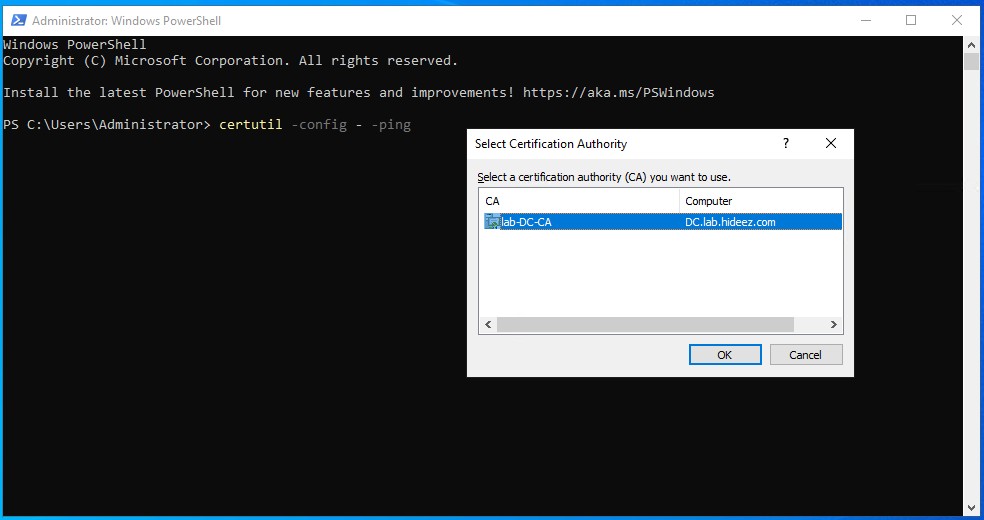
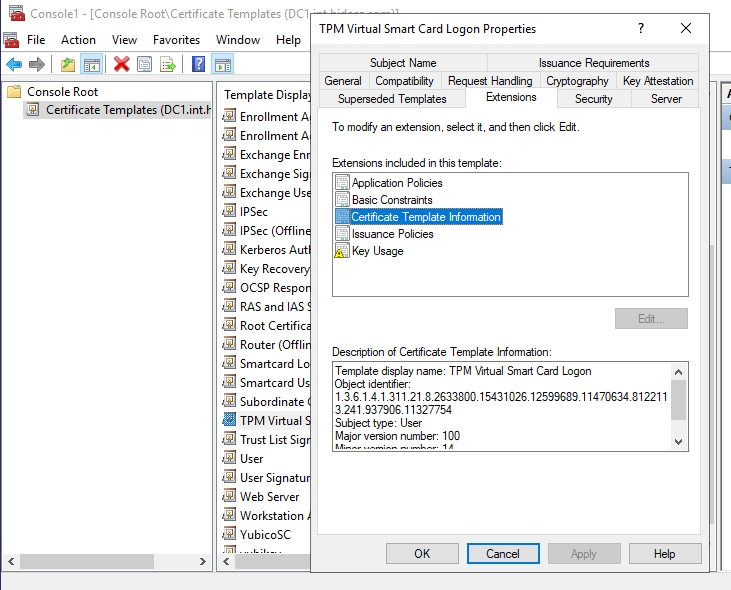
3. To define the third parameter (Certificate Template ID), go to the domain controller, and do the following:
Last updated
